Windows server 2016 Standard.
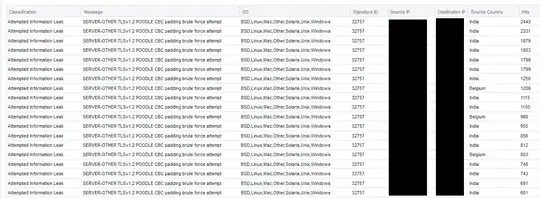
Recently we've been getting hit by brute force attempt using POODLE. I did a little research and found we should disable SSLv3. However, when I go into:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Protocols\
...and look at my SSL 3.0 key, I already have both Client and Server folders in there and both have the same two DWORDs: DisabledByDefault (1), and Enabled (0). I must have already done this in the past at one point: https://www.digicert.com/kb/ssl-support/iis-disabling-ssl-v3.htm
If I scan our site using online scanners:
https://www.poodlescan.com POODLE results: SSLv3 enabled
https://www.site24x7.com/ POODLE results: Error occurred while validating SSL3 Poodlebleed Vulnerability for domain
https://ssl-tools.net/ POODLE results: all show TLSv1.2 with SSLv3 crossed out (strikethrough'd)
So. Three different checkers with three different results. Hmmm.
Apparently I'm the only one using Windows and IIS with this issue (every reference I've found here so far is about apache and nginx), so I am posting the question. What more do I need to do to disable SSLv3 and stop this POODLE brute force attempt? This flood of traffic, when it happens, is causing our site to report 503 Service Unavailable every few minutes.