I'm setting up a dual firewall setup with a DMZ and an internal network. The servers are dedicated root servers running Debain Bullseye, all necessarily having a NIC with a public IP. In addition, servers in the DMZ have a second NIC going to a switch.
Another dedicated root server is setup as firewall (pfSense), attached to the same switch. Now I want to route all incoming traffic from each dedicated root server through this firewall by routing all traffic from the public NICs through the second NIC, then through the firewall and back.
I'm struggling with the Debian network interface configuration. Could you provide me an example config how such re-routing should be done?
UPDATE
This is my bare config at the moment (IPs are fake of course). How should I change the config in order to use the pfSense server as a gateway as suggested?
auto lo
iface lo inet loopback
iface lo inet6 loopback
auto enp8s0
iface enp8s0 inet static
address 99.23.95.122
netmask 255.255.255.192
gateway 99.23.95.1
# route 99.23.95.3/26 via 99.23.95.1
up route add -net 99.23.95.3 netmask 255.255.255.192 gw 99.23.95.1 dev enp8s0
auto enp1s0
iface enp1s0 inet static
address 10.22.0.2/24
# gateway 10.22.0.1
pointopoint 10.22.0.1
up sysctl -w net.ipv4.ip_forward=1
up route add -net 10.22.0.0/24 gw 10.22.0.1 dev enp1s0
UPDATE 2
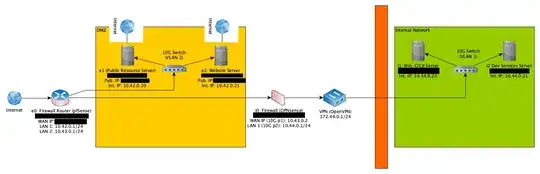
My network is as follows:
- 10GB Switch with 2 VLANs for internal network and DMZ
- External Firewall server running pfSense
- Internal firewall server running OPNsense
- 2 servers in the DMZ, each having 2 NICs: one with public IP directly connected to the provider, one private NIC connected via the Switch to same VLAN as the external firewall
- Similar setup for internal network: dedicated VLAN, two NICS. Only way to get into the internal network is via VON forwarded from external firewall to internal Firewall with VPN server on on it.
Thus what I want to achieve is to forward all incoming traffic from the two servers in the DMZ to the external firewall, before any service on the server gets it. For example, how can I configure incoming traffic to be forwarded to the internal NIC then to the firewall where it‘s filtered, and back?
UPDATE 3
Infratsucture ovierview: