I am running a dedicated High Performance AMD Server with Ubuntu 20.04. since a few months.
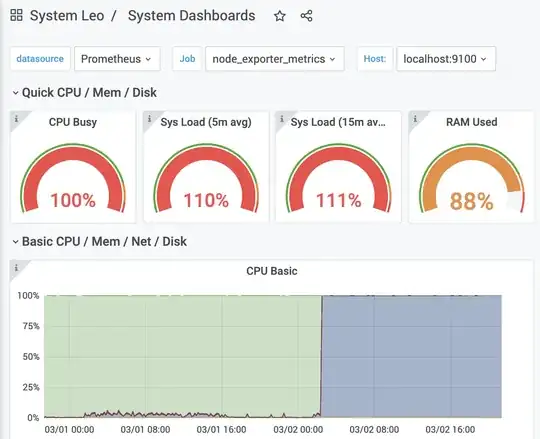
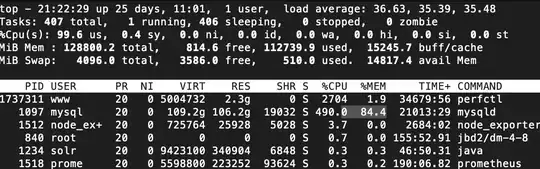
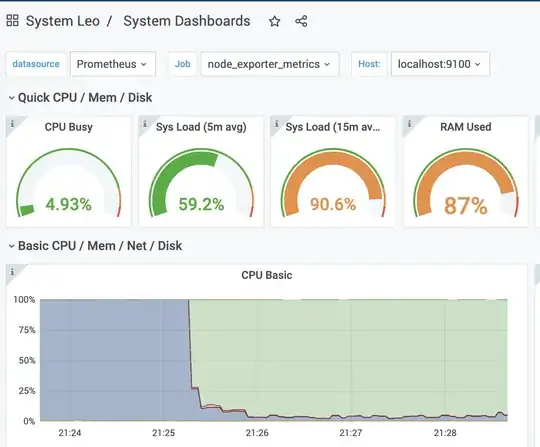
Suddenly tonight CPU shoot up to 100% until the point that I killed the service "perfctl" that appeared at 2am in the morning.
I am running Apparmor:
apparmor module is loaded.
8 profiles are loaded.
8 profiles are in enforce mode.
/usr/lib/NetworkManager/nm-dhcp-client.action
/usr/lib/NetworkManager/nm-dhcp-helper
/usr/lib/connman/scripts/dhclient-script
/usr/sbin/mysqld
/{,usr/}sbin/dhclient
lsb_release
nvidia_modprobe
nvidia_modprobe//kmod
0 profiles are in complain mode.
1 processes have profiles defined.
1 processes are in enforce mode.
/usr/sbin/mysqld (1124)
0 processes are in complain mode.
0 processes are unconfined but have a profile defined.
What could have caused this and how can this be prevented in the future?