I am trying to setup Strongswan for VPN split tunneling.
What I want is only the subnets 10.88.0.0/16 and 10.0.200.0/24 is accessible through the VPN tunnel. Everyting else is handled throught the default gateway for the network.
All clients are assigned an ip adress belonging to the 10.0.201.0/24 subnet.
In my configuration file I have among others the following:
# Default login method
eap-defaults {
remote {
auth = eap-radius
id = %any
eap_id = %any
}
}
connections
{
conn-unix : conn-defaults, eap-defaults {
children {
net {
local_ts = 10.0.200.0/24, 10.88.0.0/16
}
esp_proposals = aes128gcm128-x25519
}
pools = IkeVPN-ipv4
proposals = aes128-sha256-x25519
}
conn-windows : conn-defaults, eap-defaults {
children {
net {
local_ts = 10.0.200.0/24, 10.88.0.0/16
}
esp_proposals = aes256-sha256-prfsha256-modp1024
}
proposals = aes256-sha256-prfsha256-modp1024
pools = IkeVPN-ipv4
}
}
pools
{
IkeVPN-ipv4 {
addrs = 10.0.201.0/24
dns = 10.0.88.2
}
}
When I login over VPN it is possible to ping hosts belonging to 10.88.0.0/16 and 10.0.200.0/24, so I know I can use the VPN tunnel.
However:
If I try to access any other ressource on the Internet while still being connected to the VPN, then I cannot even ping the ip adress belonging to that ressourse.
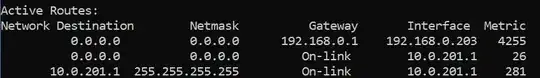
In my routing table on my Windows computer I can find the following entries:
I know that when you have two routes to a given subnet like 0.0.0.0/0 in the routing table, then whatever rule has the lowest metric wins and traffic is forwarded using that rule.
However I do not want the VPN server to install a default route via VPN, but rather only tell that the subnets 10.88.0.0/16 and 10.0.200.0/24 has to be routed via VPN.
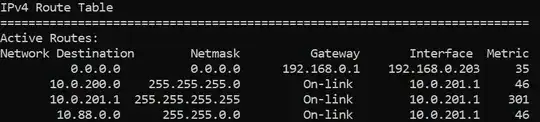
What I want is that I see a routing table closer to this without having to edit the routing table by hand on every VPN client:
So how do I go about doing that?