I have the following UniFi based network. For the context of this question, all statements relate to IPv6 connectivity unless otherwise stated.
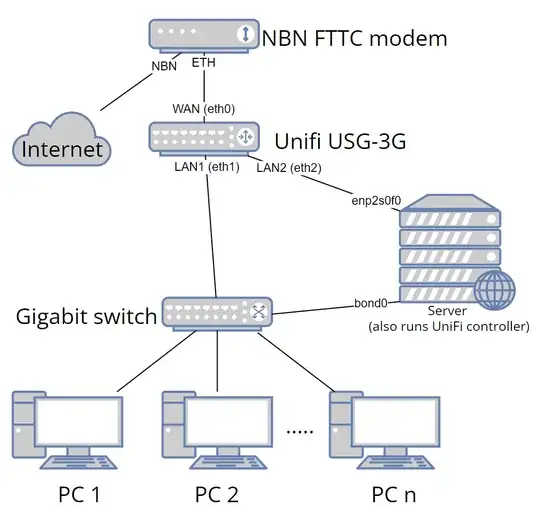
In this setup, the server can access the internet through the USG via bond0, but cannot do so via enp2s0f0. In addition, the USG and server cannot ping each other between LAN2/enp2s0f0, however they can between LAN1/bond0. No firewall has been installed on the server.
IPv4 connectivity and internet access between LAN2/enp2s0f0 works without issue.
All interfaces on the USG and server have both link-local and global IPv6 addresses, assigned via prefix delegation. The USG receives a WAN IP via DHCPv6 with a /48 delegated. The USG in turn offers a /64 for each of the LAN interfaces via prefix delegation (with router advertisements).
The USG has an ipv6 firewall rule in the 'WAN IN' group, specifying the server's enp2s0f0 IP and two ports (80 and 443).
My objectives:
- Have server access internet via enp2s0f0 interface only.
- Have server accessible from the internet on ports 80 and 443.
Further information from the USG:
$ /sbin/ifconfig
eth0 Link encap:Ethernet HWaddr 74:ac:b9:df:d9:b8
inet addr:XXX.XXX.XXX.XXX Bcast:XXX.XXX.XXX.XXX Mask:255.255.252.0
inet6 addr: XXXX:XXXX:7fff:89:eadc:1152:90c2:550/128 Scope:Global
inet6 addr: fe80::76ac:b9ff:fedf:d9b8/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:214886 errors:0 dropped:148 overruns:0 frame:0
TX packets:154122 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:255100029 (243.2 MiB) TX bytes:18676153 (17.8 MiB)
eth1 Link encap:Ethernet HWaddr 74:ac:b9:df:d9:b9
inet addr:192.168.118.118 Bcast:192.168.118.255 Mask:255.255.255.0
inet6 addr: fe80::76ac:b9ff:fedf:d9b9/64 Scope:Link
inet6 addr: XXXX:XXXX:8b:2:76ac:b9ff:fedf:d9b9/64 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:229284 errors:0 dropped:183 overruns:0 frame:0
TX packets:257854 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:25017796 (23.8 MiB) TX bytes:259257297 (247.2 MiB)
eth2 Link encap:Ethernet HWaddr 74:ac:b9:df:d9:ba
inet addr:192.168.253.1 Bcast:192.168.253.255 Mask:255.255.255.0
inet6 addr: fe80::76ac:b9ff:fedf:d9ba/64 Scope:Link
inet6 addr: XXXX:XXXX:8b:1:76ac:b9ff:fedf:d9ba/64 Scope:Global
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:10589 errors:0 dropped:0 overruns:0 frame:0
TX packets:8973 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2233148 (2.1 MiB) TX bytes:1494400 (1.4 MiB)
$ ip -6 route
XXXX:XXXX:8b:1::/64 dev eth2 proto kernel metric 256
XXXX:XXXX:8b:2::/64 dev eth1 proto kernel metric 256
XXXX:XXXX:7fff:89:eadc:1152:90c2:550 dev eth0 proto kernel metric 256
fe80::/64 dev eth0 proto kernel metric 256
fe80::/64 dev eth1 proto kernel metric 256
fe80::/64 dev eth2 proto kernel metric 256
default via fe80::2a2:ff:feb2:c2 dev eth0 proto ra metric 1024 expires 1674sec hoplimit 64
$ show firewall
--------------------------------------------------------------------------------
IPv4 Firewall "AUTHORIZED_GUESTS":
Inactive - Not applied to any interfaces, zones or for content-inspection.
rule action proto packets bytes
---- ------ ----- ------- -----
10000 drop all 0 0
--------------------------------------------------------------------------------
IPv4 Firewall "GUEST_IN":
Active on (eth2,IN)
rule action proto packets bytes
---- ------ ----- ------- -----
3001 accept tcp_udp 0 0
condition - tcp dpt:domain
3002 accept tcp 0 0
condition - tcp dpt:https match-set captive_portal_subnets dst
3003 accept all 0 0
condition - match-set guest_pre_allow dst
3004 drop all 0 0
condition - match-set guest_restricted dst
3005 drop all 0 0
condition - match-set corporate_network dst
3006 drop all 0 0
condition - match-set remote_user_vpn_network dst
3007 drop all 0 0
condition - match-set authorized_guests dst
6001 accept all 8878 1883939
condition - saddr 192.168.253.0/24
10000 accept all 0 0
--------------------------------------------------------------------------------
IPv4 Firewall "GUEST_LOCAL":
Active on (eth2,LOCAL)
rule action proto packets bytes
---- ------ ----- ------- -----
3001 accept tcp_udp 1096 80696
condition - tcp dpt:domain
3002 accept icmp 0 0
3003 accept udp 26 8528
condition - udp spt:bootpc dpt:bootps
10000 drop all 1 227
--------------------------------------------------------------------------------
IPv4 Firewall "GUEST_OUT":
Active on (eth2,OUT)
rule action proto packets bytes
---- ------ ----- ------- -----
6001 accept all 7504 1268333
condition - daddr 192.168.253.0/24
10000 accept all 0 0
--------------------------------------------------------------------------------
IPv4 Firewall "LAN_IN":
Active on (eth1,IN)
rule action proto packets bytes
---- ------ ----- ------- -----
2000 reject all 0 0
condition - state INVALID,NEW,RELATED,ESTABLISHED match-SRC--GROUP NETv4_eth2
match-DST--GROUP NETv4_eth1 reject-with icmp-port-unreachable
6001 accept all 107548 8539102
condition - saddr 192.168.118.0/24
10000 accept all 0 0
--------------------------------------------------------------------------------
IPv4 Firewall "LAN_LOCAL":
Active on (eth1,LOCAL)
rule action proto packets bytes
---- ------ ----- ------- -----
10000 accept all 30710 2348326
--------------------------------------------------------------------------------
IPv4 Firewall "LAN_OUT":
Active on (eth1,OUT)
rule action proto packets bytes
---- ------ ----- ------- -----
4000 reject all 0 0
condition - state INVALID,NEW,RELATED,ESTABLISHED match-SRC--GROUP NETv4_eth1
match-DST--GROUP NETv4_eth2 reject-with icmp-port-unreachable
6001 accept all 69747 81090972
condition - daddr 192.168.118.0/24
10000 accept all 0 0
--------------------------------------------------------------------------------
IPv4 Firewall "WAN_IN":
Active on (eth0,IN)
rule action proto packets bytes
---- ------ ----- ------- -----
3001 accept all 76607 82323027
condition - state RELATED,ESTABLISHED
3002 drop all 0 0
condition - state INVALID
3003 accept tcp 65 3404
condition - daddr lemur.dmz.XXX.XXX tcp dpt:http
3004 accept tcp 47 2472
condition - daddr lemur.dmz.XXX.XXX tcp dpt:https
3005 accept tcp 481 28276
condition - daddr lemur.dmz.XXX.XXX tcp dpt:ssh
10000 drop all 0 0
--------------------------------------------------------------------------------
IPv4 Firewall "WAN_LOCAL":
Active on (eth0,LOCAL)
rule action proto packets bytes
---- ------ ----- ------- -----
3001 accept all 6498 791616
condition - state RELATED,ESTABLISHED
3002 drop all 76 5449
condition - state INVALID
10000 drop all 1384 67100
--------------------------------------------------------------------------------
IPv4 Firewall "WAN_OUT":
Active on (eth0,OUT)
rule action proto packets bytes
---- ------ ----- ------- -----
4000 reject all 48670 3341424
condition - state INVALID,NEW,RELATED,ESTABLISHED match-SRC-ADDR-GROUP 6042f0f
26ca20408a0bf892f reject-with icmp-port-unreachable
10000 accept all 67739 7082221
--------------------------------------------------------------------------------
IPv6 Firewall "AUTHORIZED_GUESTSv6":
Inactive - Not applied to any interfaces, zones or for content-inspection.
rule action proto packets bytes
---- ------ ----- ------- -----
10000 drop all 0 0
--------------------------------------------------------------------------------
IPv6 Firewall "GUESTv6_IN":
Active on (eth2,IN)
rule action proto packets bytes
---- ------ ----- ------- -----
3001 drop all 0 0
condition - match-set corporate_networkv6 dst
10000 accept all 25 2256
--------------------------------------------------------------------------------
IPv6 Firewall "GUESTv6_LOCAL":
Active on (eth2,LOCAL)
rule action proto packets bytes
---- ------ ----- ------- -----
3001 accept udp 0 0
condition - udp dpt:domain
3002 accept icmp 0 0
10000 drop all 618 48352
--------------------------------------------------------------------------------
IPv6 Firewall "GUESTv6_OUT":
Active on (eth2,OUT)
rule action proto packets bytes
---- ------ ----- ------- -----
10000 accept all 114 9064
--------------------------------------------------------------------------------
IPv6 Firewall "LANv6_IN":
Active on (eth1,IN)
rule action proto packets bytes
---- ------ ----- ------- -----
10000 accept all 78533 8511294
--------------------------------------------------------------------------------
IPv6 Firewall "LANv6_LOCAL":
Active on (eth1,LOCAL)
rule action proto packets bytes
---- ------ ----- ------- -----
10000 accept all 837 140990
--------------------------------------------------------------------------------
IPv6 Firewall "LANv6_OUT":
Active on (eth1,OUT)
rule action proto packets bytes
---- ------ ----- ------- -----
10000 accept all 130345 168214132
--------------------------------------------------------------------------------
IPv6 Firewall "WANv6_IN":
Active on (eth0,IN)
rule action proto packets bytes
---- ------ ----- ------- -----
2000 accept ipv6-icmp 0 0
condition - state NEW,RELATED,ESTABLISHED ipv6-icmp address-unreachable
2001 accept ipv6-icmp 0 0
condition - state NEW,RELATED,ESTABLISHED ipv6-icmp packet-too-big
2002 accept ipv6-icmp 1 108
condition - state NEW,RELATED,ESTABLISHED ipv6-icmp time-exceeded
2003 accept ipv6-icmp 0 0
condition - state NEW,RELATED,ESTABLISHED ipv6-icmp parameter-problem
2004 accept tcp 0 0
condition - match-DST--GROUP 620f1fefada79301557fab76 match-set 620f1fd7ada793
01557fab75 dst LOG enabled
3001 accept all 40640 50664212
condition - state RELATED,ESTABLISHED
3002 drop all 15 900
condition - state INVALID
10000 drop all 38 4528
--------------------------------------------------------------------------------
IPv6 Firewall "WANv6_LOCAL":
Active on (eth0,LOCAL)
rule action proto packets bytes
---- ------ ----- ------- -----
3001 accept ipv6-icmp 187 13464
condition - ipv6-icmp neighbour-advertisement
3002 accept ipv6-icmp 0 0
condition - ipv6-icmp neighbour-solicitation
3003 accept all 43 5272
condition - state RELATED,ESTABLISHED
3004 accept udp 20 3460
condition - udp spt:dhcpv6-server dpt:dhcpv6-client
3005 accept ipv6-icmp 40 2880
condition - ipv6-icmp router-advertisement
3006 drop all 0 0
condition - state INVALID
10000 drop all 60 6240
--------------------------------------------------------------------------------
IPv6 Firewall "WANv6_OUT":
Active on (eth0,OUT)
rule action proto packets bytes
---- ------ ----- ------- -----
2000 accept tcp 0 0
condition - match-DST--GROUP 620f1fefada79301557fab76 match-set 620f1fd7ada793
01557fab75 dst
10000 accept all 78479 8507790
And from the server:
# /sbin/ifconfig
bond0: flags=5187<UP,BROADCAST,RUNNING,MASTER,MULTICAST> mtu 1500
inet 192.168.118.254 netmask 255.255.255.0 broadcast 192.168.118.255
inet6 fe80::508d:a7ff:fe73:e07a prefixlen 64 scopeid 0x20<link>
inet6 XXXX:XXXX:8b:2:508d:a7ff:fe73:e07a prefixlen 64 scopeid 0x0<global>
ether 52:8d:a7:73:e0:7a txqueuelen 1000 (Ethernet)
RX packets 3638275406 bytes 4719003770323 (4.2 TiB)
RX errors 0 dropped 8 overruns 0 frame 0
TX packets 2162159554 bytes 190882816640 (177.7 GiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
bond0:0: flags=5187<UP,BROADCAST,RUNNING,MASTER,MULTICAST> mtu 1500
inet 192.168.118.2 netmask 255.255.255.0 broadcast 192.168.118.255
ether 52:8d:a7:73:e0:7a txqueuelen 1000 (Ethernet)
enp2s0f0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.253.2 netmask 255.255.255.0 broadcast 192.168.253.255
inet6 fe80::d685:64ff:fe6b:703c prefixlen 64 scopeid 0x20<link>
inet6 XXXX:XXXX:8b:1:d685:64ff:fe6b:703c prefixlen 64 scopeid 0x0<global>
ether d4:85:64:6b:70:3c txqueuelen 1000 (Ethernet)
RX packets 4407 bytes 711568 (694.8 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5408 bytes 1111010 (1.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
# ip -6 route
::1 dev lo proto kernel metric 256 pref medium
XXXX:XXXX:8b:1::/64 dev enp2s0f0 proto kernel metric 256 expires 86107sec pref medium
XXXX:XXXX:8b:2::/64 dev bond0 proto kernel metric 256 expires 86289sec pref medium
fe80::/64 dev bond0 proto kernel metric 256 pref medium
fe80::/64 dev enp2s0f0 proto kernel metric 256 pref medium
default via XXXX:XXXX:b9ff:fedf:d9b9 dev bond0 proto ra metric 1024 expires 1689sec hoplimit 64 pref high
default via XXXX:XXXX:b9ff:fedf:d9ba dev enp2s0f0 proto ra metric 1024 expires 1507sec hoplimit 64 pref high
# cat /etc/network/interfaces
auto lo bond0 enp2s0f0
## The loopback network interface
iface lo inet loopback
## NBN via USG
iface enp2s0f0 inet dhcp
iface enp2s0f0 inet6 auto
## LAN
iface bond0 inet static
address 192.168.118.254
netmask 255.255.255.0
slaves enp2s0f1 enp3s0f0
bond-mode balance-rr
bond-miimon 100
bond-downdelay 200
bond-updelay 200
iface bond0 inet6 auto
## don't use bond as default gateway
accept_ra 0
post-up ip -6 route del default via fe80::76ac:b9ff:fedf:d9b9 dev bond0
## Cache
auto bond0:0
iface bond0:0 inet static
address 192.168.118.2
netmask 255.255.255.0
My question: Why can neither device access the other (via IPv6) on this enp2s0f0/LAN2 link?
This question seemed to have a comparable objective, but unfortunately was unanswered.