Nginx is configured as load balancer and has a server certificate installed to terminater TLS handshake for MQTT connections. It works when TLS extensions are included in clientHello during the handshake but there are other clients running old code who don't send any TLS extensions in clientHello. In that case I found Nginx will throw errors as in
SSL_do_handshake() failed (SSL: error:14201044:SSL routines:tls_choose_sigalg:internal error) while SSL handshaking, client: x.x.x.107, server: 0.0.0.0:8883
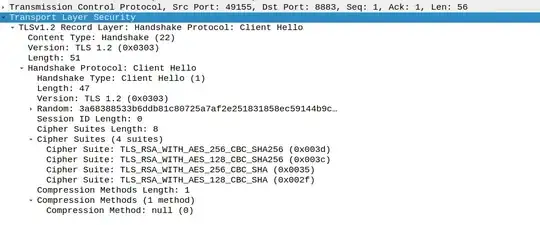
Here is Wireshark capturing
It looks to me Nginx is expecting at least the signature alorightms extension. My question is if possible Nginx can be configured to accept TLS handshake when client is not using extensions?
Nginx stream config is here (only show TLS related):
upstream brokers{
server 127.0.0.1:18831;
server 127.0.0.1:18832;
server 127.0.0.1:18833;
zone tcp_mem 64k;
hash $mqtt_client_id consistent;
}
server {
listen 8883 ssl;
preread_buffer_size 1k;
ssl_certificate /etc/nginx/certs/server.pem;
ssl_certificate_key /etc/nginx/certs/server.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_session_cache shared:SSL:128m;
ssl_session_tickets on;
ssl_session_timeout 8h;
ssl_verify_client off;
ssl_prefer_server_ciphers off;
proxy_pass brokers;
proxy_connect_timeout 5s;
access_log /var/log/nginx/mqtt_access.log mqtt;
error_log /var/log/nginx/mqtt_error.log debug;
}
Here is the wireshark captureing when clients send extensions in clientHello: