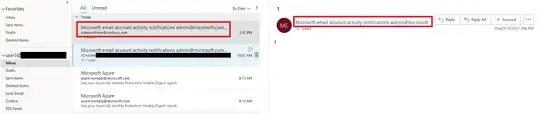
I'm trying to do phishing mitigation in the Outlook desktop app, and I've seen a number of cases where the display name is so long that the email address gets truncated, e.g.
From: Microsoft email account activity notifications admin@microsoft.completely.bogus.example.com
might get truncated in the view pane to
From: Microsoft email account activity notifications <admin@microsoft.com
which looks at least superficially legit.
Is there a way to ensure that the full email address is displayed? Yes, I know that users can mouse over the email address to see who the email is from, but I want to eliminate barriers to good email security.
Ideally, I would like to set this in a GPO.