I have two users, say userA and userB. userA can use a keytab with aes but not rc4 and userB can use a keytab with rc4 but not aes.
This is the snippet that makes the keytab, tests it, and puts it into place:
#!/bin/sh
PRINCIPAL="xxxxx"
# METHOD="rc4-hmac"
# METHOD="aes256-cts-hmac-sha1-96"
METHOD="rc4-hmac-exp"
KEYTAB="/tmp/$PRINCIPAL.keytab.$METHOD"
PASSWORD='xxxxx'
set -x
umask 0007
KEYTAB_TMP=$(mktemp "/tmp/$KEYTAB.XXXXXXXXXXXXXXXXX")
function cleanup {
rm -f "$KEYTAB_TMP"
}
trap cleanup EXIT
expect << EOF
set timeout 10
spawn /usr/bin/ktutil
expect {
"ktutil: " { send "addent -password -p $PRINCIPAL@FOO.COM -k 1 -e $METHOD\r" }
timeout { puts "Timeout waiting for ktutil prompt."; exit 1; }
}
expect {
-re "Password for \\\\S+: " { send "$PASSWORD\r" }
timeout { puts "Timeout waiting for password prompt."; exit 1; }
}
expect {
"ktutil: " { send "wkt $KEYTAB_TMP\r" }
}
expect {
"ktutil: " { send "q\r" }
}
EOF
chown "$PRINCIPAL":root "$KEYTAB_TMP"
chmod ug=rw,o= "$KEYTAB_TMP"
if [ -s "$KEYTAB_TMP" ]
then
if /usr/bin/klist -e -k -t -K "$KEYTAB_TMP"
then
if su "$PRINCIPAL" -c "env KRB5_TRACE=/tmp/krb5_trace.$PRINCIPAL.$METHOD /usr/bin/kinit $PRINCIPAL@FOO.COM -V -k -t $KEYTAB_TMP"
the
mv -f "$KEYTAB_TMP" "$KEYTAB"
fi
fi
fi
Here's the trace for userB using aes:
[28458] 1625700358.740403: Getting initial credentials for userB@FOO.COM
[28458] 1625700358.740404: Looked up etypes in keytab: aes256-cts
[28458] 1625700358.740406: Sending unauthenticated request
[28458] 1625700358.740407: Sending request (185 bytes) to FOO.COM
[28458] 1625700358.740408: Initiating TCP connection to stream 10.128.65.6:88
[28458] 1625700358.740409: Sending TCP request to stream 10.128.65.6:88
[28458] 1625700358.740410: Received answer (185 bytes) from stream 10.128.65.6:88
[28458] 1625700358.740411: Terminating TCP connection to stream 10.128.65.6:88
[28458] 1625700358.740412: Response was from master KDC
[28458] 1625700358.740413: Received error from KDC: -1765328359/Additional pre-authentication required
[28458] 1625700358.740416: Preauthenticating using KDC method data
[28458] 1625700358.740417: Processing preauth types: PA-PK-AS-REQ (16), PA-PK-AS-REP_OLD (15), PA-ETYPE-INFO2 (19), PA-ENC-TIMESTAMP (2)
[28458] 1625700358.740418: Selected etype info: etype rc4-hmac, salt "", params ""
[28458] 1625700358.740419: Retrieving userB@FOO.COM from FILE:/tmp/userB.keytab.aes256-cts-hmac-sha1-96.a148ff3d6c5ccc05f4644a2cdab2b23d (vno 0, enctype rc4-hmac) with result: -1765328203/No key table entry found for userB@FOO.COM
[28458] 1625700358.740420: Preauth module encrypted_timestamp (2) (real) returned: -1765328203/No key table entry found for userB@FOO.COM
Here it is using rc4:
[28706] 1625700362.799792: Getting initial credentials for userB@FOO.COM
[28706] 1625700362.799793: Looked up etypes in keytab: rc4-hmac-exp
[28706] 1625700362.799795: Sending unauthenticated request
[28706] 1625700362.799796: Sending request (185 bytes) to FOO.COM
[28706] 1625700362.799797: Initiating TCP connection to stream 10.128.65.6:88
[28706] 1625700362.799798: Sending TCP request to stream 10.128.65.6:88
[28706] 1625700362.799799: Received answer (185 bytes) from stream 10.128.65.6:88
[28706] 1625700362.799800: Terminating TCP connection to stream 10.128.65.6:88
[28706] 1625700362.799801: Response was from master KDC
[28706] 1625700362.799802: Received error from KDC: -1765328359/Additional pre-authentication required
[28706] 1625700362.799805: Preauthenticating using KDC method data
[28706] 1625700362.799806: Processing preauth types: PA-PK-AS-REQ (16), PA-PK-AS-REP_OLD (15), PA-ETYPE-INFO2 (19), PA-ENC-TIMESTAMP (2)
[28706] 1625700362.799807: Selected etype info: etype rc4-hmac, salt "", params ""
[28706] 1625700362.799808: Retrieving userB@FOO.COM from FILE:/tmp/userB.keytab.rc4-hmac-exp.3ddbc476378a57f4a7f4dbb700af6316 (vno 0, enctype rc4-hmac) with result: 0/Success
[28706] 1625700362.799809: AS key obtained for encrypted timestamp: rc4-hmac/B9A0
[28706] 1625700362.799811: Encrypted timestamp (for 1625700362.799810): plain 301AA011180F32303231303730373233323630325AA10502030C3442, encrypted 88F8E7E775BC3B93D0F392D9967E061B36246899F942A33EC123103A531DB6D2FB580A3C96FA97E24A74A844A41B532506F54F4C
[28706] 1625700362.799812: Preauth module encrypted_timestamp (2) (real) returned: 0/Success
[28706] 1625700362.799813: Produced preauth for next request: PA-ENC-TIMESTAMP (2)
[28706] 1625700362.799814: Sending request (260 bytes) to FOO.COM
[28706] 1625700362.799815: Initiating TCP connection to stream 10.128.65.6:88
[28706] 1625700362.799816: Sending TCP request to stream 10.128.65.6:88
[28706] 1625700362.799817: Received answer (1774 bytes) from stream 10.128.65.6:88
[28706] 1625700362.799818: Terminating TCP connection to stream 10.128.65.6:88
[28706] 1625700362.799819: Response was from master KDC
[28706] 1625700362.799820: Salt derived from principal: FOO.COMuserB
[28706] 1625700362.799821: AS key determined by preauth: rc4-hmac/B9A0
[28706] 1625700362.799822: Decrypted AS reply; session key is: aes256-cts/F217
[28706] 1625700362.799823: FAST negotiation: unavailable
[28706] 1625700362.799824: Initializing KEYRING:persistent:207:207 with default princ userB@FOO.COM
[28706] 1625700362.799825: Storing userB@FOO.COM -> krbtgt/FOO.COM@FOO.COM in KEYRING:persistent:207:207
[28706] 1625700362.799826: Storing config in KEYRING:persistent:207:207 for krbtgt/FOO.COM@FOO.COM: pa_type: 2
[28706] 1625700362.799827: Storing userB@FOO.COM -> krb5_ccache_conf_data/pa_type/krbtgt\/FOO.COM\@FOO.COM@X-CACHECONF: in KEYRING:persistent:207:207
Here's a sample of the outputs of the script for userB:
+ expect
spawn /usr/bin/ktutil
ktutil: addent -password -p userB@FOO.COM -k 1 -e aes256-cts-hmac-sha1-96
Password for userB@FOO.COM:
ktutil: wkt /tmp/userB.keytab.aes256-cts-hmac-sha1-96.873c0ce2947f8bd6caea07de0d1d02eb
ktutil: + chown userB:root /tmp/userB.keytab.aes256-cts-hmac-sha1-96.873c0ce2947f8bd6caea07de0d1d02eb
+ chmod ug=rw,o= /tmp/userB.keytab.aes256-cts-hmac-sha1-96.873c0ce2947f8bd6caea07de0d1d02eb
+ '[' -s /tmp/userB.keytab.aes256-cts-hmac-sha1-96.873c0ce2947f8bd6caea07de0d1d02eb ']'
+ /usr/bin/klist -e -k -t -K /tmp/userB.keytab.aes256-cts-hmac-sha1-96.873c0ce2947f8bd6caea07de0d1d02eb
Keytab name: FILE:/tmp/userB.keytab.aes256-cts-hmac-sha1-96.873c0ce2947f8bd6caea07de0d1d02eb
KVNO Timestamp Principal
---- ------------------- ------------------------------------------------------
1 07/09/2021 10:24:05 userB@FOO.COM (aes256-cts-hmac-sha1-96) (0xdecff4a27a46a16267567a080311195e4e33d29caf3c4a2b782d2ed53b580c14)
+ su userB -c 'env KRB5_TRACE=/tmp/krb5_trace.userB.aes256-cts-hmac-sha1-96 /usr/bin/kinit userB@FOO.COM -V -k -t /tmp/userB.keytab.aes256-cts-hmac-sha1-96.873c0ce2947f8bd6caea07de0d1d02eb'
Using existing cache: persistent:207:207
Using principal: userB@FOO.COM
Using keytab: /tmp/userB.keytab.aes256-cts-hmac-sha1-96.873c0ce2947f8bd6caea07de0d1d02eb
kinit: Pre-authentication failed: No key table entry found for userB@FOO.COM while getting initial credentials
+ expect
spawn /usr/bin/ktutil
ktutil: addent -password -p userB@FOO.COM -k 1 -e rc4-hmac-exp
Password for userB@FOO.COM:
ktutil: wkt /tmp/userB.keytab.rc4-hmac-exp.0db811bfd7e10197146bcca944b942d9
ktutil: + chown userB:root /tmp/userB.keytab.rc4-hmac-exp.0db811bfd7e10197146bcca944b942d9
+ chmod ug=rw,o= /tmp/userB.keytab.rc4-hmac-exp.0db811bfd7e10197146bcca944b942d9
+ '[' -s /tmp/userB.keytab.rc4-hmac-exp.0db811bfd7e10197146bcca944b942d9 ']'
+ /usr/bin/klist -e -k -t -K /tmp/userB.keytab.rc4-hmac-exp.0db811bfd7e10197146bcca944b942d9
Keytab name: FILE:/tmp/userB.keytab.rc4-hmac-exp.0db811bfd7e10197146bcca944b942d9
KVNO Timestamp Principal
---- ------------------- ------------------------------------------------------
1 07/09/2021 10:24:30 userB@FOO.COM (arcfour-hmac-exp) (0xd6ed7055f216ab755e1827f582b35e24)
+ su userB -c 'env KRB5_TRACE=/tmp/krb5_trace.userB.rc4-hmac-exp /usr/bin/kinit userB@FOO.COM -V -k -t /tmp/userB.keytab.rc4-hmac-exp.0db811bfd7e10197146bcca944b942d9'
Using existing cache: persistent:207:207
Using principal: userB@FOO.COM
Using keytab: /tmp/userB.keytab.rc4-hmac-exp.0db811bfd7e10197146bcca944b942d9
Authenticated to Kerberos v5
Note both traces have ..
Selected etype info: etype rc4-hmac, salt "", params ""X
But userA ends up having in both logs, which fail the OTHER way around:
Selected etype info: etype aes256-cts ...
I'm working with the kerberos admins -- it's AD. The two users are in different OU's -- can there be different policies based on OU? Is there something I should have the admins look at?
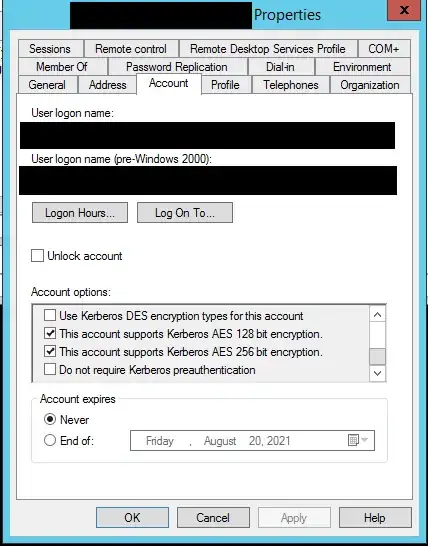 ]
]