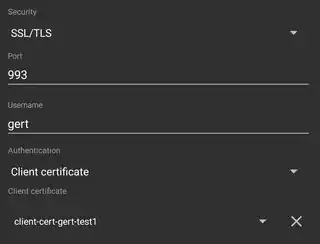
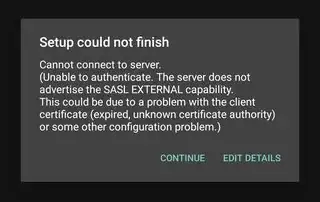
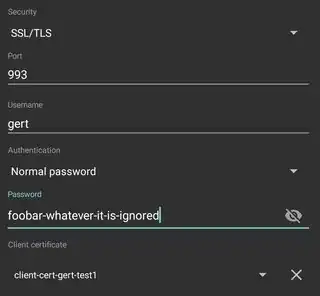
Similar to my previous Q&A in which I successfully set up an authenticating Dovecot IMAP proxy with Kerberos/GSSAPI, I want to do the same with TLS client certificates;
- My upstream (backend) IMAP server allows to authenticate without a password (trusts this Dovecot proxy to authenticate users properly).
- This Dovecot proxy is set up to validate a TLS client certificates and take the username from the Common Name field of the certificate.
The Dovecot configuration file:
# Default configuration will have it listen on IMAP tcp/143 with StartTLS required and IMAPS tcp/993 with TLS required.
protocols = imap
hostname = myhostname.domain.tld
passdb {
driver = static
# Backend IMAP server that accepts any/none password for a given user.
args = proxy=y host=10.1.2.3 port=9999 pass=masterpass nopassword=y
}
# Deliberately omitted userdb, because this is a proxy.
# local username only
auth_username_format = %n
# Logging to foreground with some verbose logging for authentication.
log_path = /dev/stderr
auth_verbose = yes
verbose_ssl = yes
auth_debug = yes
ssl = required
ssl_cert = </etc/dovecot-ssl/cert.crt
ssl_key = </etc/dovecot-ssl/key.pem
ssl_prefer_server_ciphers = yes
ssl_min_protocol = TLSv1.2
ssl_cipher_list = ECDHE-ECDSA-AES128-GCM-SHA256:[... omitted for brevity ...]
# SSL client certificate authentication required (no password required by client).
# https://doc.dovecot.org/configuration_manual/dovecot_ssl_configuration/#client-certificate-verification-authentication
ssl_ca = </etc/dovecot-ssl/client-ca.crt
ssl_verify_client_cert = yes
auth_ssl_require_client_cert = yes
# I don't have CRL set up at this point (will do later) and Dovecot requires to disable CRL check or else it fails.
ssl_require_crl = no
# Take the username from the client certificate (CN)
auth_ssl_username_from_cert = yes
ssl_cert_username_field = commonName
This works really well, except for one thing: the clients are still required to provide a bogus username/password.
I would have expected to be able to omit username/password in IMAP clients (authentication type = client cert), e.g. K-9 mail.
Server side error in logs shows a no auth attempts info level logged error message:
[...]
Apr 27 18:37:57 imap-login: Info: Received valid SSL certificate: [...]
[...]
Apr 27 18:37:57 imap-login: Debug: SSL: where=0x2002, ret=1: SSL negotiation finished successfully
Apr 27 18:37:57 imap-login: Debug: SSL alert: close notify
Apr 27 18:37:57 imap-login: Info: Disconnected (no auth attempts in 0 secs): user=<>, rip=10.9.9.9, lip=10.1.2.4, TLS, session=<Yw6fj/jA1JsKMgB0>
Apr 27 18:37:57 imap-login: Debug: SSL alert: close notify
When setting a bogus username+password, the login seems to work, though:
[...]
Apr 27 18:33:36 imap-login: Debug: SSL: where=0x2002, ret=1: SSL negotiation finished successfully
Apr 27 18:33:36 imap-login: Info: proxy(gert): started proxying to 10.1.2.3:9999: user=<gert>, method=PLAIN, rip=10.9.9.9, lip=10.1.2.4, TLS, session=<bSMSgPjA0psKMgB0>
So, bottom line my question is: how do I configure Dovecot to log in with TLS client certificate only and to avoid having to tell my users to pick a random password?
I've tried:
- setting
nologin=yas passdb arg option, but that does not seem to have any effect. - set
auth_mechanisms = anonymous, but that does not seem to have any effect. - set
auth_mechanisms =(empty), but that fails any connection withauth: Fatal: No authentication mechanisms configured