I am an SRE engineer, currently working on building a hybrid cloud network and its management. Through research, I have been able to use openvpn and wireguard topology combination network proficiently. Because wireguard can combine VPC well, and openvpn combines LDAP well (It means we can easily achieve large-scale management of people). So last week I have successfully used these two to implement an architecture that is easy for access control and personnel management.
However, there was an error in restarting the relocation server, and it has been stagnant for a long time. I don’t know if I can ask you to help determine the cause of the problem.
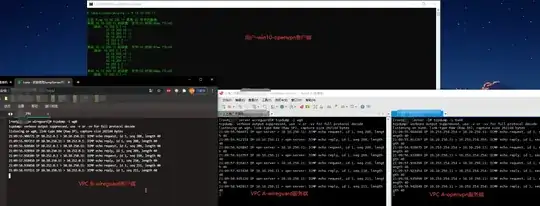
Here is the Topology:
And here is the proof of success:
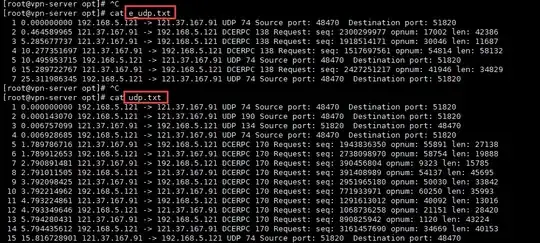
But now there is a little error, the wireguard server transmits the data packet from the openvpn server to the wireguard client, but the UDP port of the wireguard client caught the data packet, but it did not return. I currently have no ideas. Here is the packet capture situation
# openvpn server tun0
1 0.000000000 10.11.254.254 -> 192.168.5.121 ICMP 60 Echo (ping) request id=0x0001, seq=2825/2315, ttl=128
2 4.821120726 10.11.254.254 -> 192.168.5.121 ICMP 60 Echo (ping) request id=0x0001, seq=2826/2571, ttl=128
3 9.812869195 10.11.254.254 -> 192.168.5.121 ICMP 60 Echo (ping) request id=0x0001, seq=2827/2827, ttl=128
4 14.825211662 10.11.254.254 -> 192.168.5.121 ICMP 60 Echo (ping) request id=0x0001, seq=2828/3083, ttl=128
# wireguard server wg0
1 0.000000000 10.11.254.254 -> 192.168.5.121 ICMP 60 Echo (ping) request id=0x0001, seq=2825/2315, ttl=127
2 4.821113913 10.11.254.254 -> 192.168.5.121 ICMP 60 Echo (ping) request id=0x0001, seq=2826/2571, ttl=127
3 9.812859921 10.11.254.254 -> 192.168.5.121 ICMP 60 Echo (ping) request id=0x0001, seq=2827/2827, ttl=127
4 14.825202064 10.11.254.254 -> 192.168.5.121 ICMP 60 Echo (ping) request id=0x0001, seq=2828/3083, ttl=127
wireguard client
1 0.000000000 192.168.5.121 -> 121.37.167.91 UDP 74 Source port: 48470 Destination port: 51820
2 0.464589965 121.37.167.91 -> 192.168.5.121 DCERPC 138 Request: seq: 2300299977 opnum: 17002 len: 42386
3 5.285677737 121.37.167.91 -> 192.168.5.121 DCERPC 138 Request: seq: 1918514171 opnum: 30046 len: 11687
4 10.277351697 121.37.167.91 -> 192.168.5.121 DCERPC 138 Request: seq: 1517697561 opnum: 54814 len: 58132
5 10.495953715 192.168.5.121 -> 121.37.167.91 UDP 74 Source port: 48470 Destination port: 51820
6 15.289722767 121.37.167.91 -> 192.168.5.121 DCERPC 138 Request: seq: 2427251217 opnum: 41946 len: 34829
7 25.311986345 192.168.5.121 -> 121.37.167.91 UDP 74 Source port: 48470 Destination port: 51820
e_udp.txt is the result of packet capture from the openvpn client PING wireguard client; udp.txt is the normal reply packet captured from the wireguard server PING wireguard client.