The server has also httpd with PHP services running I did read the guide here: https://a1websitepro.com/find-track-filthy-spammer-block/ I did install EXIM
My client complains they never had this happen on the Windows Server 2000, 2003, 2012.
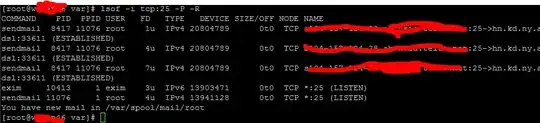
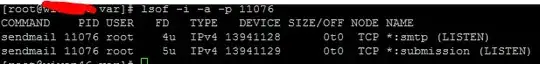
Here is a list of commands that I have run
[![enter image description here][1]][1]
Did read and try:
- https://serverfault.com/questions/647871/determine-originating-process-for-outbound-traffic
- http://www.rfxn.com/projects/linux-malware-detect/
- https://serverfault.com/questions/483650/how-to-find-which-script-on-my-server-is-sending-spam-emails
- https://ericheikes.com/tracing-spam-from-php-scripts/
- https://www.inmotionhosting.com/support/email/find-spam-script-location-with-exim/