I'm (still) trying to properly configure VLANs on a level 3 switch (Netgear GS516TP).
Basic scenario: there are three VLANs: VLAN 10, 11, and 12, with respectively three ports, and three machines.
- 10.0.10.5, connected to port g10 and belonging to VLAN 10.
- 10.0.11.5, connected to port g11 and belonging to VLAN 11.
- 10.0.12.5, connected to port g12 and belonging to VLAN 12.
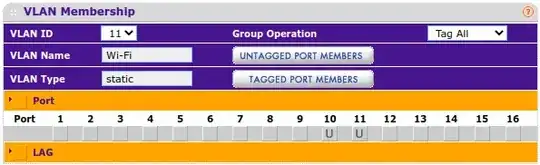
VLAN 10 has untagged ports g10, g11, and g12.
VLAN 11 has untagged ports g10 and g11. Similarly, VLAN 12 has untagged ports g10 and g12.
The goal is to be able for machines belonging to VLAN 11 and VLAN 12 to communicate with the machines in VLAN 10. However, a machine from VLAN 11 should know nothing about machines in VLAN 12 (and the other way around).
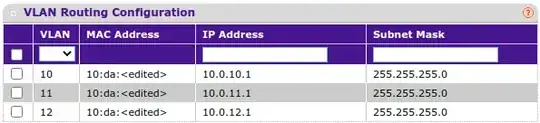
While all three machines are using the netmask 255.255.0.0, the routing configuration is set like this:
Now, the problem. When I send a TCP or UDP packet from 10.0.10.5 to 10.0.11.5 (for instance by doing nc -n 10.0.11.5 100), I can see this packet in Wireshark running on the machine which belongs to VLAN 12. It doesn't work the other way around, though, i.e. a packet sent from 10.0.11.5 is not visible in VLAN 12.
What should I do in order for the packets targeting machines from VLAN 11 to never reach the ports belonging to VLAN 12?