I want to set up multiple VLANs in order to be able to isolate different types of devices from each other. More specifically, I want to restrict what Wi-Fi devices can see when exploring the network: for instance they can access the reverse proxy through HTTP, but they shouldn't be able to access the syslog server or sniff SNMP v1/v2 traffic, nor should they know that there is a syslog server or SNMP traffic in the first place.
I'm using Netgear ProSafe smart switches to set up the VLANs. I've:
- Created the VLAN 6 for testing purposes.
- Set the corresponding switch port to the PVID 6.
- Marked the VLAN membership for this port as untagged.
- Ensured “Admit all” acceptable frame types is set for all devices for now. According to the documentation, this means that “Untagged and priority tagged frames received on the port are accepted and assigned the value of the Port VLAN ID for this port.”
- Set VLAN 6 routing IP address and mask to 192.168.252.1/24.
- Ensured the switch is set to run in routing mode.
- Reconfigured
/etc/network/interfacesof the test machines.
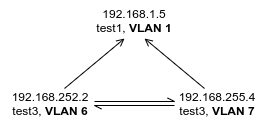
Here's a simplified view of the network:
I was expecting to be able to communicate between test2 and test1, but this is not the case. Currently:
test2:~ ping 192.168.252.1works.test2:~ ping 8.8.8.8doesn't, nor doesping 192.168.1.5orping 192.168.1.1orping 192.168.1.3.test1:~ ping 192.168.252.2doesn't work.test2:~ nc -u 192.168.1.5 53works (if 192.168.1.5 is in listening mode withnc -ul 53).test1:~ nc -u 192.168.252.2doesn't work.ncin TCP mode doesn't work in either direction.
The routing table displayed by the switch lists both VLANs in the list of learned routes, indicating the correct VLAN for each route. The same switch displays the ARP cache which contains the correct MAC addresses of all four machines.
What additional things should I do for inter-VLAN communication?