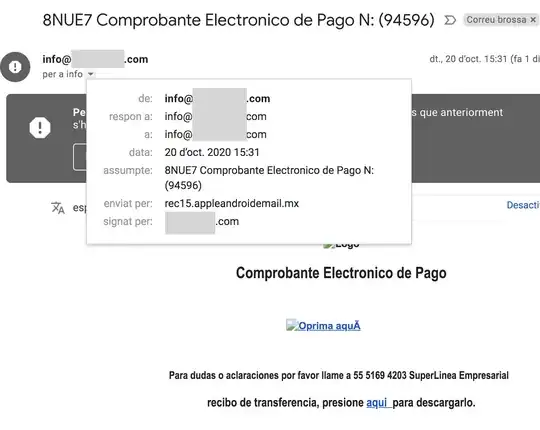
I've received an email in spam from info@mydomain.com to info@mydomain.com, but the "sent by" came from rec15.appleandrdoidmail.mx. info@mydomain.com is an alias. Weird thing is that it says is signed by mydomain.com!
I've been looking at the email source and the email passed DKIM and SPF filters (haven't found DMARC info):
Assumpte: 8NUE7 Comprobante Electronico de Pago N: (94596)
SPF: PASS amb la IP 0.0.0.0 Més informació
DKIM: 'PASS' amb el domini mydomain.com Més informació
I've been looking at the mail logs for connections and found this:
Oct 20 13:32:00 mydomain postfix/smtpd[5162]: connect from rec15.appleandroidemail.mx[45.7.231.194]
Oct 20 13:32:01 mydomain postfix/smtpd[5162]: 5A04D1B5C75: client=rec15.appleandroidemail.mx[45.7.231.194]
Oct 20 13:32:01 mydomain postfix/cleanup[5164]: 5A04D1B5C75: message-id=<20201020133159.0905B124154@rec15.appleandroidemail.mx>
Oct 20 13:32:01 mydomain postfix/qmgr[2202]: 5A04D1B5C75: from=<www-data@rec15.appleandroidemail.mx>, size=3140, nrcpt=1 (queue active)
Oct 20 13:32:01 mydomain postfix/smtpd[5162]: disconnect from rec15.appleandroidemail.mx[45.7.231.194] ehlo=1 mail=1 rcpt=1 data=1 quit=1 commands=5
Oct 20 13:32:07 mydomain postfix/smtpd[5180]: connect from mydomain.com[127.0.0.1]
Oct 20 13:32:07 mydomain postfix/smtpd[5180]: EA2481B5F8A: client=mydomain.com[127.0.0.1]
Oct 20 13:32:07 mydomain postfix/cleanup[5164]: EA2481B5F8A: message-id=<20201020133159.0905B124154@rec15.appleandroidemail.mx>
Oct 20 13:32:08 mydomain postfix/qmgr[2202]: EA2481B5F8A: from=<www-data@rec15.appleandroidemail.mx>, size=4004, nrcpt=1 (queue active)
Oct 20 13:32:08 mydomain postfix/smtpd[5180]: disconnect from mydomain.com[127.0.0.1] ehlo=1 mail=1 rcpt=1 data=1 quit=1 commands=5
Oct 20 13:32:08 mydomain amavis[16608]: (16608-05) Passed CLEAN {RelayedInbound}, [45.7.231.194]:50918 [45.7.231.194] <www-data@rec15.appleandroidemail.mx> -> <miquel@mydomain.com>, Queue-ID: 5A04D1B5C75, Message-ID: <20201020133159.0905B124154@rec15.appleandroidemail.mx>, mail_id: qwEeUiSFqmai, Hits: 3.204, size: 3164, queued_as: EA2481B5F8A, 6422 ms
Oct 20 13:32:08 mydomain postfix/smtp[5165]: 5A04D1B5C75: to=<miquel@mydomain.com>, orig_to=<info@mydomain.com>, relay=127.0.0.1[127.0.0.1]:10024, delay=6.8, delays=0.33/0.01/0/6.4, dsn=2.0.0, status=sent (250 2.0.0 from MTA(smtp:[127.0.0.1]:10025): 250 2.0.0 Ok: queued as EA2481B5F8A)
Oct 20 13:32:08 mydomain postfix/qmgr[2202]: 5A04D1B5C75: removed
Oct 20 13:32:08 mydomain dovecot: lmtp(5182): Connect from local
Oct 20 13:32:08 mydomain dovecot: lmtp(miquel@mydomain.com): 8ksOBtjmjl8+FAAAWnabiA: msgid=<20201020133159.0905B124154@rec15.appleandroidemail.mx>: saved mail to INBOX
Oct 20 13:32:08 mydomain dovecot: lmtp(5182): Disconnect from local: Successful quit
Oct 20 13:32:08 mydomain postfix/lmtp[5181]: EA2481B5F8A: to=<miquel@mydomain.com>, relay=mydomain.com[private/dovecot-lmtp], delay=0.15, delays=0.13/0.01/0.01/0.01, dsn=2.0.0, status=sent (250 2.0.0 <miquel@mydomain.com> 8ksOBtjmjl8+FAAAWnabiA Saved)
Oct 20 13:32:08 mydomain postfix/qmgr[2202]: EA2481B5F8A: removed
SPF configuration:
mydomain.com. 86400 IN TXT "v=spf1 ip4:xx.xx.xx.xx include:_spf.mydomain.com ~all"
mydomain.com. 86400 IN TXT "v=spf2.0/pra ip4:xx.xx.xx.xx include:_spf.mydomain.com ~all"
DKIM configuration:
20XXXX._domainkey.mydomain.com. 82086 IN TXT "v=DKIM1; k=rsa; p=MIGfMA0GC..."
DMARC configuration:
v=DMARC1; p=reject; pct=100; rua=mailto:abuse@mydomain.com; ruf=mailto:abuse@mydomain.com; aspf=s; adkim=s; fo=1
I've reviewed all DMARC xml reports and haven't found any entry for 45.7.231.194 IP address, neither reject, none or quarantine.
In the email source I've found:
X-Received: by 2002:a2f:a551:: with SMTP id a23mr2209527ljn.5.1603290742268;
Tue, 20 Oct 2020 06:32:24 -0700 (PDT)
Authentication-Results: mx.google.com;
spf=pass (google.com: best guess record for domain of www-data@rec15.appleandroidemail.mx designates 45.7.231.194 as permitted sender) smtp.mailfrom=www-data@rec15.appleandroidemail.mx;
dkim=pass header.i=@mydomain.com header.s=20XXXX header.b=EBPdgUba
Received-SPF: pass (google.com: best guess record for domain of www-data@rec15.appleandroidemail.mx designates 45.7.231.194 as permitted sender) client-ip=45.7.231.194;
...
Received: from localhost (mydomain.com [127.0.0.1]) by mydomain.com (Postfix) with ESMTP id EA2481B5F8A for <miquel@mydomain.com>; Tue, 20 Oct 2020 13:32:07 +0000 (UTC)
So it seems that someone authorized 45.7.231.194 to send emails in the name of mydomain.com, but I thought that SPF was for this purpose, to protect someone to use mydomain.com to send emails on its name. What I'm missing? Is there something misconfigured?
Please any help on how to block this attack will be really appreciated.