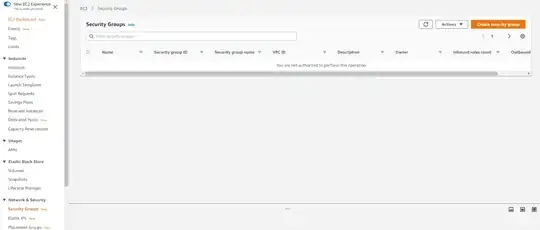
I'm trying to allow a user to modify inbound rules on one particular security group.
Here's what I tried. I thought it would be straight forward, but this doesn't work. What other permissions do I need to provide?
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"ec2:RevokeSecurityGroupIngress",
"ec2:AuthorizeSecurityGroupIngress"
],
"Resource": "arn:aws:ec2:*:1234567890:security-group/sg-0115448f9fcb00g3c"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "ec2:DescribeSecurityGroups",
"Resource": "*"
}
]
}
The authorisation to view the security groups is not happening.