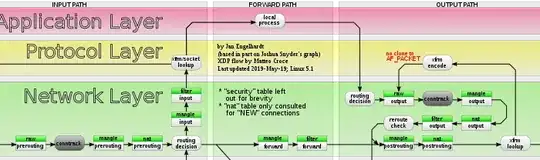
It first needs to store states. With some old BSD firewall that I used, I guess was named IPFW, I used to put a rule that sated "keep track of the state of the leaving packet", and this was placed on the outbound direction of interfaces. Then, another rule on the inbound direction that checked them against those states that were created by the rule on the outbound direction. So there used to be 2 rules: (1) to populate the states table, this was on the outbound direction, and (2) to lookup the states table, this was on the inbound direction.
But with connntrack, I see it applied on the INPUT chain, such as this rule:
iptables -A INPUT -m conntrack --ctstate RELATED,ESTABLISHED -j ACCEPT
This makes me wonder, what is that statement actually doing?
- Is it saying that it will start tracking packets that match that rule by putting their information in the states table?
- Or is it saying that it already has the states information, and it is going to act against inbound messages based on it? (e.g. accept if they belonged to a previously accepted connection?). But, in this case, where did the states table get populated? Which rule does it? Or is it rule-less and implicit?