I have a spanning tree issue on my Cisco SG500 SMB Switches that I could use some help solving.
Here is a diagram of my setup:
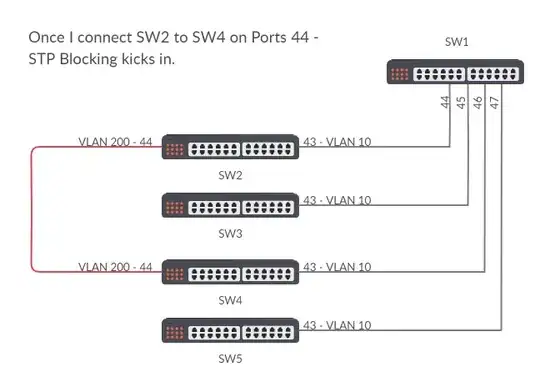
SW1 (ports 44-47, VLAN 10) connect to port 43 (VLAN 10) on SW2, SW3, SW4, SW5. When I connect SW2 (Port 44, VLAN 200) to SW4 (Port 44, VLAN 200) - STP blocks the port. I don't know why.
Below are the configuration for the 5 switches:
Switch 1
###
### Common Switch Configuration (Do Before Switch-Specific Configuration) ==
###
# First the switch needs to be in Switch mode, and Standalone mode. Check if it is or not with these two commands:
show system mode
show stack
# Place in standalone mode if not already. This will erase everything - so do this step first.
do stack standalone
do stack standalone reboot
# Answer yes to the three confirmation prompts that are displayed
# Disable Auto Config / Updates via DHCP
no boot host auto-config
no boot host auto-update
# Disable SmartPort
macro auto disabled
voice vlan state disabled
# Configure CDP (Global Settings)
cdp device-id format hostname
no cdp mandatory-tlvs validation
no cdp appliance-tlv enable
# Disable LLDP and Bonjour
no lldp run
no bonjour enable
# Set Default VLAN forbidden on all
int range ge1/1/1-52,Po1-32
switchport forbidden default-vlan
# Configure the Clock and Network-Time Protocol
clock dhcp timezone
clock source sntp
clock summer-time mdt recurring usa
sntp server 10.10.10.1 poll
sntp unicast client enable
# Use these commands verify clock operation:
show clock / show clock detail / show sntp configuration / show sntp status
###
### Configure NHS-SW1 (Management Switch)
###
# Configure CDP (Switch-Specific settings)
cdp source-interface ge1/1/48
cdp run
int range ge1/1/1,ge1/1/44-48
cdp enable
# Add VLAN 10 (Management VLAN)
vlan database
vlan 10
int vlan 10
name Management
# Configure IP Settings
int vlan 10
ip address 10.10.10.10 255.255.255.0
ip default-gateway 10.10.10.1
hostname nhs-sw1
sntp source-interface vlan10
# Enable SSH Server with Password Authentication
ip ssh server
ip ssh password-auth
# Configure Spanning Tree to use MSTP
spanning-tree
spanning-tree bpdu filtering
spanning-tree mode mst
spanning-tree mst configuration
instance 1 vlan 10
name NHS
revision 0
exit
# Configure Device Priority per MST instance
spanning-tree mst 1 priority 4096
# Port 1 is for Administrator plug in access
int ge1/1/1
switchport mode access
switchport access vlan 10
power inline never
# Disable all ports not in use
int range ge1/1/2-43,ge1/1/49-50
no cdp enable
power inline never
int range ge1/1/2-43,ge1/1/49-50,Po1-32
shutdown
# Ports 44-47 connect to other switches and carry management data.
int range ge1/1/44-47
switchport mode trunk
switchport trunk allowed vlan add 10
switchport forbidden default-vlan
power inline never
# Port 44 connects to Primary Port 43
# Port 45 connects to Aux Port 43
# Port 46 connects to Trusted Port 43
# Port 47 connects to Wifi Port 43
# Port 48 Connects to the router management port
int range ge1/1/48
switchport mode trunk
switchport trunk native vlan 10
switchport forbidden default-vlan
power inline never
# Configure MST on Trunking Ports
int range ge1/1/44-48
spanning-tree portfast
no spanning-tree bpdu
no spanning-tree guard root
no spanning-tree bpduguard
# Configure MSTP on Edge Ports
int range ge1/1/1-43,ge1/1/49-50,Po1-32
no spanning-tree bpdu
spanning-tree guard root
spanning-tree bpduguard enable
spanning-tree portfast
spanning-tree mst 1 port-priority 128
# Set MST Port Priority on Trunking Ports
int ge1/1/48
spanning-tree mst 1 port-priority 16
int ge1/1/46
spanning-tree mst 1 port-priority 32
int ge1/1/44
spanning-tree mst 1 port-priority 48
int ge1/1/47
spanning-tree mst 1 port-priority 64
int ge1/1/45
spanning-tree mst 1 port-priority 80
# Configure Logging
no logging aggregation on
aaa logging login
file-system logging
logging source-interface ge1/1/43
logging host 10.10.10.1 port 514
logging origin-id string "NHS-SW1 (Mgmt)"
Switch 2
###
### Common Switch Configuration (Do Before Switch-Specific Configuration) ==
###
# First the switch needs to be in Switch mode, and Standalone mode. Check if it is or not with these two commands:
show system mode
show stack
# Place in standalone mode if not already. This will erase everything - so do this step first.
do stack standalone
do stack standalone reboot
# Answer yes to the three confirmation prompts that are displayed
# Disable Auto Config / Updates via DHCP
no boot host auto-config
no boot host auto-update
# Disable SmartPort
macro auto disabled
voice vlan state disabled
# Configure CDP (Global Settings)
cdp device-id format hostname
no cdp mandatory-tlvs validation
no cdp appliance-tlv enable
# Disable LLDP and Bonjour
no lldp run
no bonjour enable
# Set Default VLAN forbidden on all
int range ge1/1/1-52,Po1-32
switchport forbidden default-vlan
# Configure the Clock and Network-Time Protocol
clock dhcp timezone
clock source sntp
clock summer-time mdt recurring usa
sntp server 10.10.10.1 poll
sntp unicast client enable
# Use these commands verify clock operation:
show clock / show clock detail / show sntp configuration / show sntp status
#
# Configure NHS-SW2 (Primary Switch)
#
# Configure CDP (Switch-Specific settings)
cdp source-interface ge1/1/43
cdp run
int ge1/1/1-42,ge1/1/44-48
no cdp enable
# Set Default VLAN forbidden on all
int range ge1/1/1-52,Po1-32
switchport forbidden default-vlan
# Add VLANs: 10 (Management), 16 (Guest), 32 (Printers), 100 (ChromeNet), 200 (Trusted)
vlan database
vlan 10,16,32,100,200
int vlan 10
name Management
# Configure IP Settings
ip address 10.10.10.11 255.255.255.0
ip default-gateway 10.10.10.1
hostname nhs-sw2
sntp source-interface vlan10
# Enable SSH Server with Password Authentication
ip ssh server
ip ssh password-auth
# Configure remaining VLANs
interface vlan 16
name Guest
interface vlan 32
name Printers
interface vlan 100
name ChromeNet
interface vlan 200
name Trusted
exit
# Configure Spanning Tree to use MST
spanning-tree
spanning-tree bpdu filtering
spanning-tree mode mst
spanning-tree mst configuration
instance 1 vlan 10
instance 3 vlan 16
instance 4 vlan 32
instance 5 vlan 100
instance 6 vlan 200
name NHS
revision 0
exit
# Configure Device Priority per MST instance
spanning-tree mst 1 priority 8192
spanning-tree mst 3 priority 8192
spanning-tree mst 4 priority 8192
spanning-tree mst 5 priority 8192
spanning-tree mst 6 priority 8192
# Disable all ports not in use
int range ge1/1/19-24,ge1/1/47-50
no cdp enable
power inline never
int range ge1/1/19-24,ge1/1/47-50,Po1-32
shutdown
# Ports 1-6 and 25-30 are for Wifi. Since the Unifi Access points use the default vlan for their management traffic - we define a native vlan here.
int range ge1/1/1-6,ge1/1/25-30
switchport mode trunk
switchport trunk native vlan 10
switchport trunk allowed vlan add 16
switchport trunk allowed vlan add 32
switchport trunk allowed vlan add 100
switchport trunk allowed vlan add 200
switchport forbidden default-vlan
power inline auto
# Ports 7-12 and 31-36 are for printers
int range ge1/1/7-12,ge1/1/31-36
switchport mode access
switchport access vlan 32
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 16
switchport forbidden vlan add 100
switchport forbidden vlan add 200
power inline never
# Ports 13-18 and 37-42 are for trusted devices
int range ge1/1/13-18,ge1/1/37-42
switchport mode access
switchport access vlan 200
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 16
switchport forbidden vlan add 32
switchport forbidden vlan add 100
power inline never
# Port 43 Connects to the Management Switch port 44
int ge1/1/43
switchport mode trunk
switchport trunk allowed vlan add 10
switchport forbidden default-vlan
switchport forbidden vlan add 16
switchport forbidden vlan add 32
switchport forbidden vlan add 100
switchport forbidden vlan add 200
power inline never
# Port 44 Connects to the Trusted Switch port 44
int ge1/1/44
switchport mode trunk
switchport trunk allowed vlan add 200
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 16
switchport forbidden vlan add 32
switchport forbidden vlan add 100
power inline never
# Port 45 Connects to the Wifi Switch on port 45. This trunks Guest and ChromeNet - but not Trusted
int ge1/1/45
switchport mode trunk
switchport trunk allowed vlan add 16
switchport trunk allowed vlan add 100
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 32
switchport forbidden vlan add 200
power inline never
# Port 46 Connects to the Auxiliary Switch on port 45. This trunks printer data
int ge1/1/46
switchport mode trunk
switchport trunk allowed vlan add 32
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 16
switchport forbidden vlan add 100
switchport forbidden vlan add 200
power inline never
# Configure Spanning Tree options on Trunking Ports
int range ge1/1/43-46
spanning-tree portfast
no spanning-tree bpdu
no spanning-tree guard root
no spanning-tree bpduguard
# Configure MSTP on Edge Ports
int range ge1/1/1-42,ge1/1/47-50,Po1-32
no spanning-tree bpdu
spanning-tree guard root
spanning-tree bpduguard enable
spanning-tree portfast
# Set MST Port Priority on Trunking Ports
int ge1/1/43
spanning-tree mst 1 port-priority 48
int ge1/1/45
spanning-tree mst 3 port-priority 32
spanning-tree mst 5 port-priority 32
int ge1/1/46
spanning-tree mst 4 port-priority 32
int ge1/1/44
spanning-tree mst 6 port-priority 48
# Set MST Port Priority on Edge Ports
int range ge1/1/1-42,ge1/1/47-50,Po1-32
# Configure Logging
no logging aggregation on
aaa logging login
file-system logging
logging source-interface ge1/1/43
logging host 10.10.10.1 port 514
logging origin-id string "NHS-SW2 (Pri)"
Switch 3
###
### Common Switch Configuration (Do Before Switch-Specific Configuration) ==
###
# First the switch needs to be in Switch mode, and Standalone mode. Check if it is or not with these two commands:
show system mode
show stack
# Place in standalone mode if not already. This will erase everything - so do this step first.
do stack standalone
do stack standalone reboot
# Answer yes to the three confirmation prompts that are displayed
# Disable Auto Config / Updates via DHCP
no boot host auto-config
no boot host auto-update
# Disable SmartPort
macro auto disabled
voice vlan state disabled
# Configure CDP (Global Settings)
cdp device-id format hostname
no cdp mandatory-tlvs validation
no cdp appliance-tlv enable
# Disable LLDP and Bonjour
no lldp run
no bonjour enable
# Set Default VLAN forbidden on all
int range ge1/1/1-52,Po1-32
switchport forbidden default-vlan
# Configure the Clock and Network-Time Protocol
clock dhcp timezone
clock source sntp
clock summer-time mdt recurring usa
sntp server 10.10.10.1 poll
sntp unicast client enable
# Use these commands verify clock operation:
show clock / show clock detail / show sntp configuration / show sntp status
##
## Configure NHS-SW3 (Auxillary Switch)
##
# Configure CDP (Switch-Specific settings)
cdp source-interface ge1/1/43
cdp run
int range ge1/1/1-42,ge1/1/44-48
no cdp enable
# Add VLANs: 10 (Management), 16 (Guest), 32 (Printers), 100 (ChromeNet), 200 (Trusted)
vlan database
vlan 10,14,32
int vlan 10
name Management
# Configure IP Settings
ip address 10.10.10.12 255.255.255.0
ip default-gateway 10.10.10.1
hostname nhs-sw3
sntp source-interface vlan10
# Enable SSH Server with Password Authentication
ip ssh server
ip ssh password-auth
# Configure remaining VLANs
interface vlan 14
name BMS
interface vlan 32
name Printers
# Configure Spanning Tree to use MST
spanning-tree
spanning-tree bpdu filtering
spanning-tree mode mst
spanning-tree mst configuration
instance 1 vlan 10
instance 2 vlan 14
instance 4 vlan 32
name NHS
revision 0
exit
# Configure Device Priority per MST instance
spanning-tree mst 1 priority 8192
spanning-tree mst 2 priority 4096
spanning-tree mst 4 priority 4096
# Disable all ports not in use
int range ge1/1/47,ge1/1/49-50
no cdp enable
power inline never
int range ge1/1/47,ge1/1/49-50,Po1-32
shutdown
# Ports 1-6 are BMS ports - connected to BMS devices
int range ge1/1/1-6
switchport mode access
switchport access vlan 14
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 32
power inline never
# Ports 7-42 are connected to printers needing to be accessed across multiple networks
int range ge1/1/7-42
switchport mode access
switchport access vlan 32
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 14
power inline never
# Port 43 Connects to the Management Switch port 45
int ge1/1/43
switchport mode trunk
switchport trunk allowed vlan add 10
switchport forbidden default-vlan
switchport forbidden vlan add 14
switchport forbidden vlan add 32
power inline never
# Port 44 is connected to the router and carries BMS data
int ge1/1/44
switchport mode trunk
switchport trunk native vlan 14
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 32
power inline never
# Port 45 Connects to the primary switch on port 46 carries printer data
int ge1/1/45
switchport mode trunk
switchport trunk allowed vlan add 32
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 14
power inline never
# Port 46 Connects to the wifi switch on port 44 and carries printer data
int ge1/1/46
switchport mode trunk
switchport trunk allowed vlan add 32
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 14
power inline never
# Port 48 Connects to the router printer port
int ge1/1/48
switchport mode trunk
switchport trunk native vlan 32
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 14
power inline never
# Configure Spanning Tree options on Trunking Ports
int range ge1/1/43-46,ge1/1/48
spanning-tree portfast
no spanning-tree bpdu
no spanning-tree guard root
no spanning-tree bpduguard
# Configure MSTP on Edge Ports
int range ge1/1/1-42,ge1/1/47,ge1/1/49-50,Po1-32
no spanning-tree bpdu
spanning-tree guard root
spanning-tree bpduguard enable
spanning-tree portfast
# Set MST Port Priority on Trunking Ports
int ge1/1/43
spanning-tree mst 1 port-priority 80
int ge1/1/44
spanning-tree mst 2 port-priority 16
int ge1/1/48
spanning-tree mst 4 port-priority 16
int ge1/1/45
spanning-tree mst 4 port-priority 32
int ge1/1/46
spanning-tree mst 4 port-priority 48
# Configure Logging
no logging aggregation on
aaa logging login
file-system logging
logging source-interface ge1/1/43
logging host 10.10.10.1 port 514
logging origin-id string "NHS-SW3 (Aux)"
Switch 4
###
### Common Switch Configuration (Do Before Switch-Specific Configuration) ==
###
# First the switch needs to be in Switch mode, and Standalone mode. Check if it is or not with these two commands:
show system mode
show stack
# Place in standalone mode if not already. This will erase everything - so do this step first.
do stack standalone
do stack standalone reboot
# Answer yes to the three confirmation prompts that are displayed
# Disable Auto Config / Updates via DHCP
no boot host auto-config
no boot host auto-update
# Disable SmartPort
macro auto disabled
voice vlan state disabled
# Configure CDP (Global Settings)
cdp device-id format hostname
no cdp mandatory-tlvs validation
no cdp appliance-tlv enable
# Disable LLDP and Bonjour
no lldp run
no bonjour enable
# Set Default VLAN forbidden on all
int range ge1/1/1-52,Po1-32
switchport forbidden default-vlan
# Configure the Clock and Network-Time Protocol
clock dhcp timezone
clock source sntp
clock summer-time mdt recurring usa
sntp server 10.10.10.1 poll
sntp unicast client enable
# Use these commands verify clock operation:
show clock / show clock detail / show sntp configuration / show sntp status
##
## Configure NHS-SW4 (Trusted Switch)
##
# Configure CDP (Switch-Specific settings)
cdp source-interface ge1/1/43
cdp run
int range ge1/1/1-42,ge1/1/44-48
no cdp enable
# Add VLANs: 10 (Management), 200 (Trusted)
vlan database
vlan 10,200
# Configure VLAN 10
int vlan 10
name Management
# Configure IP Settings
ip address 10.10.10.13 255.255.255.0
ip default-gateway 10.10.10.1
hostname nhs-sw4
sntp source-interface vlan10
# Enable SSH Server with Password Authentication
ip ssh server
ip ssh password-auth
# Configure remaining VLANs
interface vlan 200
name Trusted
# Configure Spanning Tree to use MST
spanning-tree
spanning-tree bpdu filtering
spanning-tree mode mst
spanning-tree mst configuration
instance 1 vlan 10
instance 6 vlan 200
name NHS
revision 0
exit
# Configure Device Priority per MST instance
spanning-tree mst 1 priority 8192
spanning-tree mst 6 priority 4096
# Disable all ports not in use
int range ge1/1/45,ge1/1/47,ge1/1/49-50
no cdp enable
power inline never
int range ge1/1/45,ge1/1/47,ge1/1/49-50,Po2-32
shutdown
# Ports 1-40 are connected to devices that are on the trusted network
int range ge1/1/1-40
switchport mode access
switchport access vlan 200
switchport forbidden default-vlan
switchport forbidden vlan add 10
power inline never
# Ports 41-42 are aggregated and connect to the NAS
interface range ge1/1/41-42
no negotiation
channel-group 1 mode auto
port-channel load-balance src-dst-mac
interface port-channel 1
flowcontrol on
description LAG1
switchport mode access
switchport access vlan 200
switchport forbidden default-vlan
switchport forbidden vlan add 10
# Port 43 Connects to the Management Switch on port 46
int ge1/1/43
switchport mode trunk
switchport trunk allowed vlan add 10
switchport forbidden default-vlan
switchport forbidden vlan add 200
power inline never
# Port 44 Connects to the primary switch on port 44 and trunks trusted data
int ge1/1/44
switchport mode trunk
switchport trunk allowed vlan add 200
switchport forbidden default-vlan
switchport forbidden vlan add 10
power inline never
# Port 46 Connects to the wifi switch on port 46 and trunks trusted data
int ge1/1/46
switchport mode trunk
switchport trunk allowed vlan add 200
switchport forbidden default-vlan
switchport forbidden vlan add 10
power inline never
# Port 48 Connects to the router trusted port
int ge1/1/48
switchport mode trunk
switchport trunk native vlan 200
switchport forbidden default-vlan
switchport forbidden vlan add 10
power inline never
# Configure Spanning Tree options on Trunking Ports
int range ge1/1/43-44,ge1/1/46,ge1/1/48
spanning-tree portfast
no spanning-tree bpdu
no spanning-tree guard root
no spanning-tree bpduguard
# Configure MSTP on Edge Ports
int range ge1/1/1-42,ge1/1/47,ge1/1/49-50,Po1-32
no spanning-tree bpdu
spanning-tree guard root
spanning-tree bpduguard enable
spanning-tree portfast
# Set MST Port Priority on Trunking Ports
int ge1/1/43
spanning-tree mst 1 port-priority 32
int ge1/1/48
spanning-tree mst 6 port-priority 16
int Po1
spanning-tree mst 6 port-priority 32
int ge1/1/44
spanning-tree mst 6 port-priority 48
int ge1/1/46
spanning-tree mst 6 port-priority 64
# We need to restart the switch to complete the LACP setup
end
write
reload
# Configure LACP on LAG1
interface range ge1/1/41-42
lacp port-priority 1
lacp timeout long
exit
lacp system-priority 1
# Verify LACP Operation
show interfaces port-channel 1
show lacp ge1/1/41 statistics
show lacp port-channel 1
# Configure Logging
no logging aggregation on
aaa logging login
file-system logging
logging source-interface ge1/1/43
logging host 10.10.10.1 port 514
logging origin-id string "NHS-SW4 (Trusted)"
Switch 5
###
### Common Switch Configuration (Do Before Switch-Specific Configuration) ==
###
# First the switch needs to be in Switch mode, and Standalone mode. Check if it is or not with these two commands:
show system mode
show stack
# Place in standalone mode if not already. This will erase everything - so do this step first.
do stack standalone
do stack standalone reboot
# Answer yes to the three confirmation prompts that are displayed
# Disable Auto Config / Updates via DHCP
no boot host auto-config
no boot host auto-update
# Disable SmartPort
macro auto disabled
voice vlan state disabled
# Configure CDP (Global Settings)
cdp device-id format hostname
no cdp mandatory-tlvs validation
no cdp appliance-tlv enable
# Disable LLDP and Bonjour
no lldp run
no bonjour enable
# Set Default VLAN forbidden on all
int range ge1/1/1-52,Po1-32
switchport forbidden default-vlan
# Configure the Clock and Network-Time Protocol
clock dhcp timezone
clock source sntp
clock summer-time mdt recurring usa
sntp server 10.10.10.1 poll
sntp unicast client enable
# Use these commands verify clock operation:
show clock / show clock detail / show sntp configuration / show sntp status
##
## Configure NHS-SW5 (Wifi Switch)
##
# Configure CDP (Switch-Specific settings)
cdp source-interface ge1/1/43
cdp run
int range ge1/1/1-42,ge1/1/44-48
no cdp enable
# Add VLANs: 10 (Management), 16 (Guest), 32 (Printers), 100 (ChromeNet), 200 (Trusted)
vlan database
vlan 10,16,32,100,200
int vlan 10
name Management
# Configure IP Settings
ip address 10.10.10.14 255.255.255.0
ip default-gateway 10.10.10.1
hostname nhs-sw5
sntp source-interface vlan10
# Enable SSH Server with Password Authentication
ip ssh server
ip ssh password-auth
# Configure remaining VLANs
interface vlan 16
name Guest
interface vlan 32
name Printers
interface vlan 100
name ChromeNet
interface vlan 200
name Trusted
# Configure Spanning Tree to use MST
spanning-tree
spanning-tree bpdu filtering
spanning-tree mode mst
spanning-tree mst configuration
instance 1 vlan 10
instance 3 vlan 16
instance 4 vlan 32
instance 5 vlan 100
instance 6 vlan 200
name NHS
revision 0
exit
# Configure Device Priority per MST instance
spanning-tree mst 1 priority 8192
spanning-tree mst 3 priority 4096
spanning-tree mst 4 priority 8192
spanning-tree mst 5 priority 4096
spanning-tree mst 6 priority 8192
# Disable all ports not in use
int range ge1/1/49-50,Po1-32
no cdp enable
power inline never
int range ge1/1/49-50,Po1-32
shutdown
# Ports 1-42 are for Wifi. Since the Unifi Access points use the default vlan as their management port - we define a native vlan here.
int range ge1/1/1-42
switchport mode trunk
switchport trunk native vlan 10
switchport trunk allowed vlan add 16
switchport trunk allowed vlan add 32
switchport trunk allowed vlan add 100
switchport trunk allowed vlan add 200
switchport forbidden default-vlan
power inline auto
# Port 43 Connects to the Management Switch on port 47
int ge1/1/43
switchport mode trunk
switchport trunk allowed vlan add 10
switchport forbidden default-vlan
switchport forbidden vlan add 16
switchport forbidden vlan add 32
switchport forbidden vlan add 100
switchport forbidden vlan add 200
power inline never
# Port 44 Connects to the Auxillary Switch on port 46 and trunks printer data
int ge1/1/44
switchport mode trunk
switchport trunk allowed vlan add 32
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 16
switchport forbidden vlan add 100
switchport forbidden vlan add 200
power inline never
# Port 45 Connects to the Primary Switch on port 45 and trunks Guest and ChromeNet - but not Trusted
int ge1/1/45
switchport mode trunk
switchport trunk allowed vlan add 16
switchport trunk allowed vlan add 100
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 32
switchport forbidden vlan add 200
power inline never
# Port 46 Connects to the Trusted Switch on port 46 and trunks Trusted
int ge1/1/46
switchport mode trunk
switchport trunk allowed vlan add 200
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 16
switchport forbidden vlan add 32
switchport forbidden vlan add 100
power inline never
# Port 47 connects to the router on the Guest port
int ge1/1/47
switchport mode trunk
switchport trunk native vlan 16
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 32
switchport forbidden vlan add 100
switchport forbidden vlan add 200
power inline never
# Port 48 connects to the router on the ChromeNet port
int ge1/1/48
switchport mode trunk
switchport trunk native vlan 100
switchport forbidden default-vlan
switchport forbidden vlan add 10
switchport forbidden vlan add 16
switchport forbidden vlan add 32
switchport forbidden vlan add 200
power inline never
# Configure Spanning Tree options on Trunking Ports
int range ge1/1/43-44,ge1/1/46,ge1/1/48
spanning-tree portfast
no spanning-tree bpdu
no spanning-tree guard root
no spanning-tree bpduguard
# Configure MSTP on Edge Ports
int range ge1/1/1-42,ge1/1/47,ge1/1/49-50,Po1-32
no spanning-tree bpdu
spanning-tree guard root
spanning-tree bpduguard enable
spanning-tree portfast
spanning-tree mst port-priority 128
# Set MST Port Priority on Trunking Ports
int ge1/1/43
spanning-tree mst 1 port-priority 64
int ge1/1/47
spanning-tree mst 3 port-priority 16
int ge1/1/45
spanning-tree mst 3 port-priority 32
int ge1/1/44
spanning-tree mst 4 port-priority 48
int ge1/1/48
spanning-tree mst 5 port-priority 16
int ge1/1/44
spanning-tree mst 6 port-priority 32
# Configure Logging
no logging aggregation on
aaa logging login
file-system logging
logging source-interface ge1/1/43
logging host 10.10.10.1 port 514
logging origin-id string "NHS-SW5 (Wifi)"