We are experiencing an issue on our classic Azure VM running Windows Server 2012 R2 when accessing www.linked.com.
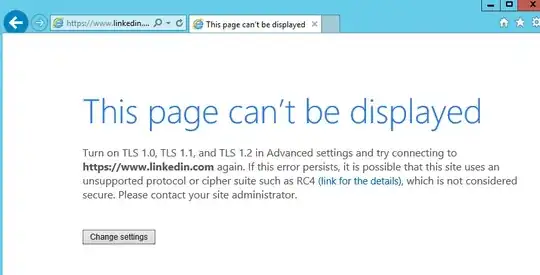
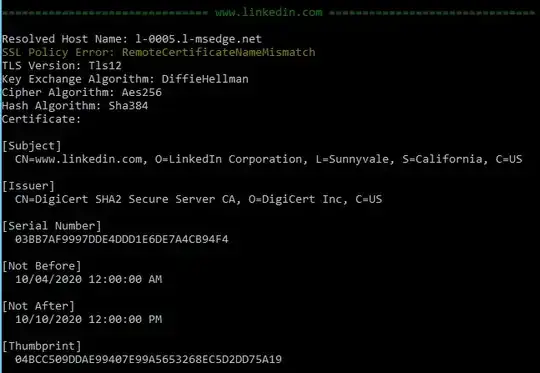
We have some applications running on IIS and talking with LinkedIn OAuth API thats where we noticed the problem. But simply trying to access www.linkedin.com in IE we get the following:
The following is an error we get in .NET application:
We went through a lot of internet resources related to changing registry keys, applying updates, etc. but no luck. We discovered that accessing the same site on a new type of Azure VM, hosted in the same region, is no problem at all. Same registry settings, same IE security settings but the classic VM still refuses to open the site.
It seems like a component sitting above the classic VM isn't resolving the network requests correctly. This has started only in the past few days as it worked absolutely fine in the past.
Other TLS 1.2 enabled websites like Google or Office365 open up with no problem on either of the VMs.
Any suggestion, ideas - much appreciated.
What was attempted to fix the issue:
- Followed the instructions in the IE error window.
- Used IISCrypto to confirm TLS settings.
- Updated/checked Windows registry settings suggested here and here (as well as other websites suggesting similar things).
- Mainly tried to find the difference between classic and new Azure type VMs when a network request goes out using WireShark and a few other tools.
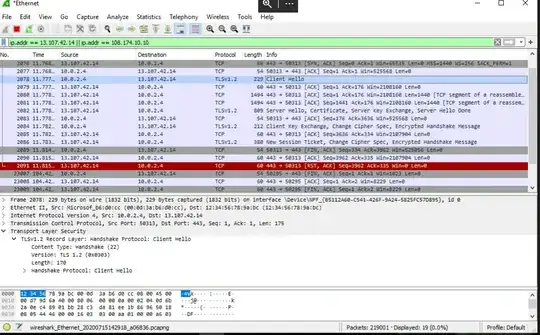
Here is Wireshark output of a request being made from a new type of VM (where IE has no issue opening linkedin.com) (screenshot includes ClientHello TLS content).
And here is the same request in the classic VM
Not a 100% sure what that is telling me but maybe will help someone when sharing their insights.