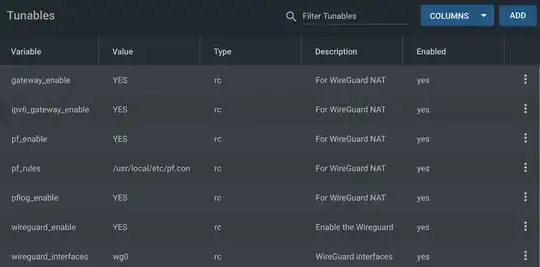
In addition to WireGuard also enable the FreeBSD packet filter pf using rc.conf tunables:
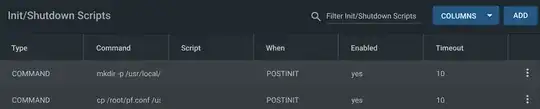
iXsystems recommends wg0.conf to live in /root and a Post Init Script to copy it to a system location then start WireGuard:
mkdir -p /usr/local/etc/wireguard && cp /root/wg0.conf /usr/local/etc/wireguard/wg0.conf && /usr/local/etc/rc.d/wireguard start
By default pf is configured via /etc/pf.conf, but we need to follow the above pattern and copy /root/pf.conf to /usr/local/etc/pf.conf on startup and have pf use that.
My pf.conf follows. WireGuard IP addresses are arbitrary on an arbitrary subnet. pf will route and NAT from this subnet to the rest of the network. I don't know of a way to do this without these arbitrary, but static, IP addresses.
# Interfaces
ext_if = "igb0"
wireguard_if = "wg0"
# Wireguard Settings
wireguard_net_v4 = "192.168.222.0/24"
wireguard_net_v6 = "fc::0/64"
# Rules must be in order: options, normalization, queueing, translation, filtering
# Options
set skip on lo
# Translation
# Nat all wireguard to non-wireguard traffic
nat on $ext_if inet from $wireguard_net_v4 to { any, !$wireguard_net_v4 } -> ($ext_if)
#nat on $ext_if inet6 from $wireguard_net_v6 to { any, !$wireguard_net_v6 } -> {$ext_if}
# Filtering
pass inet all
pass inet6 all
(uncomment the ipv6 NAT if your ipv6 works)
My FreeNAS server's wg0.conf:
[Interface]
PrivateKey = foofafi
ListenPort = 51820
Address = 192.168.222.1/32, fc::1/64
[Peer]
PublicKey = CLIENT1_PUBLIC_KEY
AllowedIPs = 192.168.222.2/32, fc::2/128
Laptop client configuration:
[Interface]
PrivateKey = blahblahblah
Address = 192.168.222.2/32
DNS = 1.1.1.1
[Peer]
PublicKey = SERVER_PUBLIC_KEY
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = dynamicdns.example.com:51820
PersistentKeepalive = 25
Thanks to https://gist.github.com/apearson/168b244b4735cceff9809ef3d07f4df5 for a nearly working config!
See also pf docs and this.

