We are running a Domino server (V 10.0.1 FP3) hosting a number of Xpages applications. Apart from the admins all users are accessing those application through http only (i.e., no nrpc / Notes client access).
The users' person data are synched from AD to Domino via TDI. Authentication is done against the company's AD, this is configured through a Web SSO config document. There however is no complete SSO set up so that users will have to authenticate when first accessing the applications through their browsers.
For application related reasons we set the Ltpa token's expiration time to a rather high value (if necessary I am willing to discuss the reasons for that in a separate thread, but this is not really related to this question here).
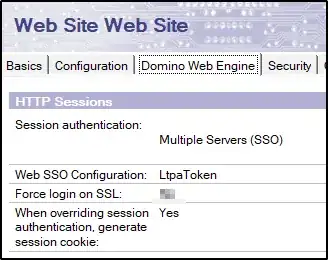
Here's a screenshot of the config page:
Domino's http task is restarted every morning at 2:30 through a program document issueing
restart task http
Some observations from that server, both using admin client / internet users view and tell http show users issued at the server console:
- an http restart apparently doesn't invalidate the tokens, i.e. once the http is back up a user who kept the browser open can easily continue accessing the applications without having to re-authenticate (within the expiration time frame). (EDIT): This appears to be true even if the entire domino server is restarted
- if users simply close their browsers instead of correctly logging off the tokens at the server side aren't removed (again, as long as they don't expire). If then the user logs on again a 2nd /3rd / 4th token for this user appears server-side
- there's apparently no direct way to drop a user session, neither through a simple
dropconsole command nor through admin client actions
Question: are there ways to drop those user sessions from the server side and/or truly invalidate the tokens? Basically, what I'm looking for is a way to make sure that users have to re-authenticate every morning. As http is restarted at 2:30 every morning (see above) it would be ideal to also do this at or around that time.
Update 2020-03-30:
for completeness: for this server we use an Internet site document which is setup like this: