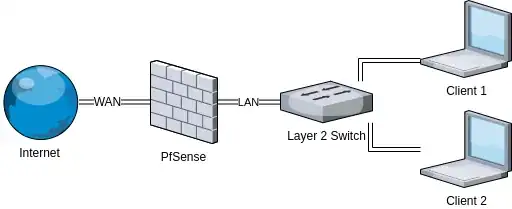
A "layer 2 switch" is really a switch, i.e., its only task is to forward network frames from one net branch to the other. But with today's plummeting hardware costs, many devices called "switch" have lots of additional features (like handling VLANs, faking separate networks using the same box -- essentially allowing you to separate the switch into several separate ones; filtering traffic using a variety of criteria), up to and working as routers (connecting separate networks, routing traffic as required). Often you get a "switch" that is really a router, and those generally have the smarts (hardware-wise) to do traffic filtering (i.e., act as a firewall).
For example, the "access point" or "cable modem" box you have at home is really a router and WiFi access point (connects a cabled network to WiFi) plus a firewall (doing at least NAT). If you take a peek, handling WiFi is very complex business (some channels can not be used, depending on the country; need to connect to the network and handle encrypted traffic; need to hand over from one access point to another as you move through a large building; ...), and all that is done in a WiFi card that today costs a few bucks.