Since there's absolutely no way to tell what's inside that file and what it's capable of, I'd recommend cutting your losses and nuking it from the get-go. With most PDFs (and, infact, any file really) you can recover relatively quickly as the PDF is bound to reside somewhere else (either an earlier draft or an un-modified version).
That being said, you seem very keen to open this PDF so I'm assuming it has some sort of uniqueness to it. You'll need to forgive me for putting my day-job hat on but usually this means a user hasn't saved or backed up their documents when they should have. If that's not the case, and this is truly the Dead Sea Scrolls of the PDF world, let's see how we can open/clean these files without damaging them or, indeed, yourself.
Using a browser to recover the PDF
You've brought up opening them in a browser several times:
"Upload the document to Google Docs. I assume that Google has one of the most secure PDF viewers out there."
and
"Use Firefox's pdf.js or some other browser-based viewer"
As I said at the beginning, we've no idea what we're dealing with at the moment. Opening it a browser (at this stage) wouldn't be recommended. Also uploading it to Google is a little bit unethical since you know full well that there's something suspicious going on with the PDF.
Even if you were somehow able to know exactly what that PDF file's malicious content is capable of, there's no way to ensure it hasn't been tampered with to masquerade.
Using a VM/isolated machine to recover the PDF
You touched on it in the middle of your question, using a VM or isolated machine is obviously a far safer way of opening that PDF.
Now you might be thinking that's a lot of time to spend setting one of those up but if you keep a snapshot of clean, portable, small systems taken immediately after the installation has completed, we can almost safely open the PDF, print the contents to file (as @KnightOfNi has already alluded to) without the PDF editing capabilities. Why not go one step further and actually print them on a closed loop with a USB printer and rescan them? Might seem like a massive hassle but we're dealing with a time-bomb of unknown magnitude. It could destroy your system, steal your data, crypto-locker your stuff, or simply be a lemon - the point is we have no idea.
"Can I be sure that it is safe?"
From your question:
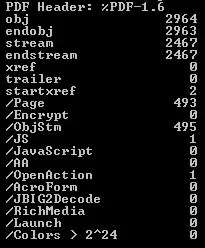
Another question I have: How reliable is the pdfid tool? For example, if I get a result with no Javascript, OpenAction, etc. can I be sure that it is safe?
Again, not really - but there are ways you can test to see how accurate the tool is.
- If it's Open Source, have a dig through the code and make sure it's not just spitting out any old garbage and barely touching the files.
- In that VM/isolated machine lab, why not throw it some good/bad/ugly files that are known to be infected with a certain strain of malware? You can roll your own or you can reach out to the researcher community who usually have a few examples to download online.
To be honest, it all depends on how much you want to recover that PDF. For most people- it's way more hassle than it's worth... but then again, that depends on the contents.
What I'd do:
- Isolated virtual machine on an isolated physical machine (sounds like overkill but that's how I tested my first experience with CryptoLocker - glad I did it that way).
- That means no file sharing (i.e. share desktop -> desktop on VM)
- Go for an odd OS. The odder the better. Most of these PDF viruses are targeting specific users of specific versions of an operating system. I doubt they've thought about Kali, TAILS, or similar
- Deactivate plugins/delete any known areas or apps of concern (flash, etc.)
- Open a test PDF and set all the security settings to max before opening the target document
- Open the target document, physically print it, scan it back in.