History seems to have come almost full circle where old issues are shown in new/emerging technologies.
Background
If you trust the operating system, Windows originally had the Control - Alt - Delete as a way to prevent TSR (Terminate and Stay Resident) programs from stealing passwords. It also invoked a GINA now the Windows Secure Subsystem (whatever it's called these days).
If you trust the browser, Web browsers proved security using SSL/TLS/HTTPS icons in the browser, and sometimes they colored the status bar green for sites that overpaid for their SSL certificate.
Problem
Now that mobile devices don't display a HTTPS status bar when navigating it's impossible to tell if you're on a legit site, or hacked via SSLStrip MITM or HTTPS. On top of that, there isn't a secure mode integrated into the OS itself, therefore it seems next to impossible to distinguish a legit authentication dialog from an imposter.
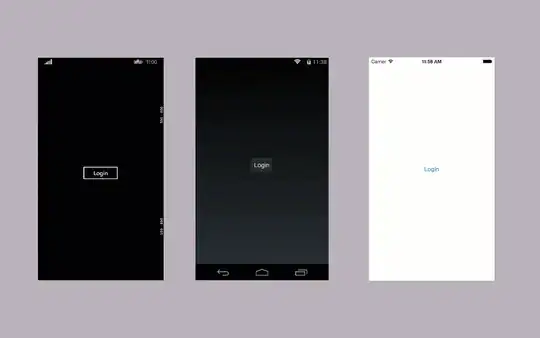
Can you tell the imposter from the legit dialog?
Although I demonstrate Azure Active Directory federation above, the same issue applies to consumer and corporate accounts that leverage other systems (OAuth, OpenID, Facebook, Ping Identity, ADFS)
This issue came to my mind as I downloaded an Android app that was clearly phishing for my credentials so it could post a favorable review of itself. ... a App Review Worm of sorts.
Question
How can a dumb end user protect themselves from such an attack, on a mobile device?
Are physical certificates the only option to prevent phishing? (TLS Mutual Auth)
Does FIDO play a role in securing the mobile space?