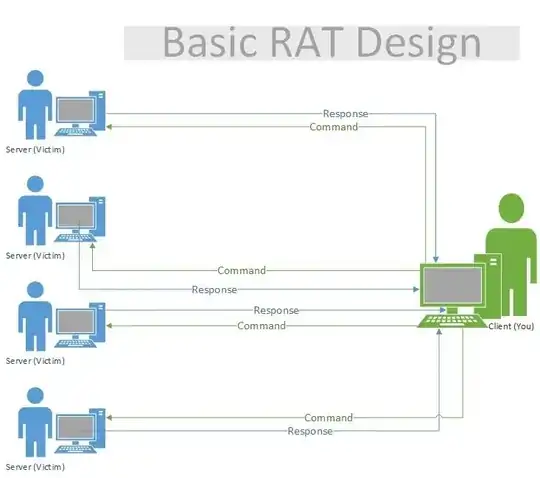
It isn't better nor worse, it depends on whether the machines you will be compromising will have publicly routable IPs or not.
If they have, then the advantage of them listening and being the server is that you can connect to them from anywhere and your controller/command and control computer doesn't need to be always connected to them - it only talks to them where there is an actual command.
If the target computers don't have a publicly routable IP, as most home computers do (they're behind a NAT), then it's better for your controller computer to be the server and the compromised machines to connect to it, however that has the downside of being less sneaky (a permanent, outgoing connection is more likely to be noticed than a rare, incoming connection like in the first scenario) and your controller computer needs to be always reachable at the same IP - if it suddenly changes, and you have no way of going back to the old IP to regain control of your bots and tell them the new IP, then you lost your bots unless you have another way of contacting them.
Personally though, I'd recommend using a P2P protocol for this - similar to Tor, where bots are interconnected and relay commands to themselves, that way you have no central point of failure and you only need to reach any single bot to control the entire botnet, since it will relay your command to everyone else. Make sure to use signatures, crypto and steganography if possible, to hide your traffic and preventing someone (like security researchers) from forging valid commands and taking control of your botnet.