I'm having an issue with my syntax to brute force my own account on a server for testing and reporting purposes to protect the rest of the community at hand.
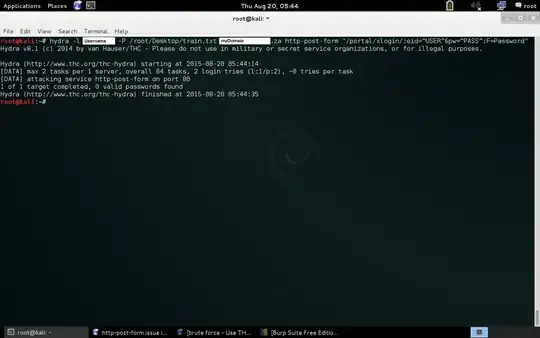
hydra -l username -P /root/Desktop/Test.txt url.zz.za http-post-form "/portal/xlogin/:ed=^USER^&pw=^PASS^:F=Invalid"
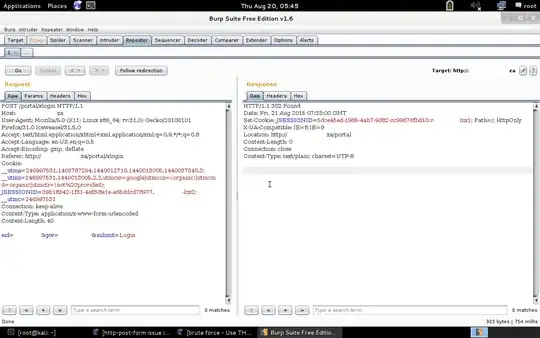
I have used "FireForce" plugin for Firefox with a successful result in getting the password from a +-20 or so word list on my Desktop. I however now would like to move to a large wordlist but I am having issues doing this. I have attached screenshots of my Hydra code, my Intercept code as well as my results for a successful login and a failed login. Can someone examine this and provide feedback on this issue?
*Notice: In FireForce where my failed message should be I have to re-reference the URL to the login page in order to pick it up as a failed attempt. It seems that the page redirects itself if it has passed the brute force test. Details on my username/password can be provided personally if need be.
It seems the form that I'm using has unlimited retries and never times out or blocks my requests when using Fireforce or manual testing.