Email is historically considered insecure for two reasons:
- The SMTP network protocol is unencrypted unless STARTTLS is negotiated, which is effectively optional
- The mail messages sit unencrypted on the disk of the source, destination, and any intermediate mail servers
Google mail servers all speak STARTTLS if possible, so for gmail-to-gmail the transmission step shouldn't be a concern. However, the sending server stores an unencrypted copy of the email in your Sent folder. The receiving server stores an unencrypted copy in the recipient's Inbox. This leaves them open to various threats:
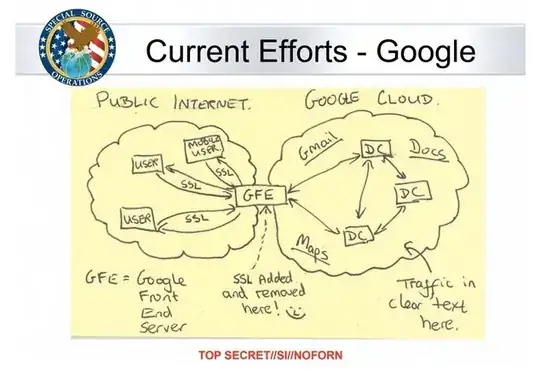
- Rogue Google employees reading that email
- Google choosing to read that email despite their assurances to the contrary
- Governments forcing Google to hand over that email
- Hackers breaking into Google and accessing that email
If you can trust everything to go right, then gmail-to-gmail is perfectly secure. But you can't always expect everything to go right.
For these reasons, the security and privacy community long ago reached the stance that only end-to-end email encryption is secure. That means the email remains encrypted on server disks and is decrypted when you're reading it, and never stored decrypted.
There have been an enormous number of comments, so let me expand/clarify a few things.
End-to-end encryption - in the context of email, when I say end-to-end encryption I mean something like PGP, where the message is encrypted until it reaches the recipient's email client, and only decrypted to be read. Yes, this means it can't be searched on the server, and often also means it doesn't remain "backed up" on the server either. This is a case where security and functionality are at odds; pick one.
Security and privacy community - unlike many Information Security topics, email security is one that extends out to other communities. The question of what stateful inspection in a firewall means is not something often extended out to interest others, for example. But email security is of direct, significant interest to
Forget about credit card data, there are people trying to communicate with email whose lives, and the lives of their families, depend upon the security of the email. So as there are phrases in the comments below like "depends upon what your standards are for 'secure'", "sufficiently motivated adversary", "there is an illusion of security at the email-level" - am I being too strong to say the server can't be trusted? Not for people whose lives are at stake. That's why the phrase "email is insecure" has been the mantra of the privacy movement for 20 years.
Trusting the server - In the US, "your cap for liability for unauthorized charges on a credit card is $50" so you may well be happy trusting the server with your credit card. If you're cheating, on the other hand, you might lose a lot more as the result of leaving unencrypted email on the server. And will your service provider shut their doors to protect your privacy? Probably not.
STARTTLS - STARTTLS is SSL for email; it uses the same SSL/TLS cryptographic protocol to encrypt email in transit. However, it is decidedly less secure than HTTPS for several reasons:
- STARTTLS is almost always "opportunistic", meaning that if the client asks and the server supports it, they'll encrypt; if either of those things are not true, the email will quietly go through unencrypted.
- Self-signed, expired, and otherwise bogus certificates are generally accepted by email senders, so STARTTLS provides confidentiality but almost none of the authentication. It's relatively trivial to Man-In-The-Middle email if you can get in between servers on the network.