Whenever a hosted script on a website tries to access a file on a user's computer the sandbox prevents it, but has there been any documented case where this sandbox obstacle was somehow overcome by the script?
2 Answers
To keep you up-to date, you can read about the freshly MFSA2015-78 where Firefox sandboxing mechanism is bypassed by violating the same origin policy. The problem fixed by Mozilla Firefox on the 6th of August 2015. This vulnerability allows attackers to bypass the same-origin policy and execute malicious JS code remotely that will be interpreted in the local file context. This, in turn, allows attackers to read and write files on local machine as well as upload them to a remote server.
Attacks exploiting this vulnerability impacts Windows, Linux and OS X operating systems.
The malicious script violates Firefox sandboxing mechanism by exploiting vulnerabilities of the embedded PDF.js in Firefox.
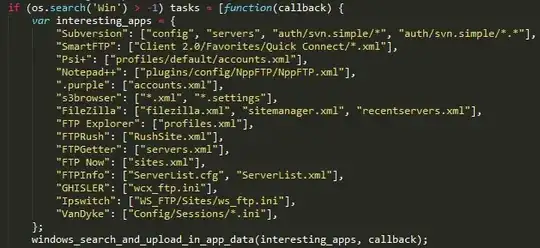
For example, in Windows OS, the script probes important configuration files to fetch, mainly for credentials. A part of its code looks like this:
You can see the list of the files in which it is interested once your browser is compromised by it.
For Internet Explorer, you may read about CVE-2015-0016 released by the end of January 2015. The vulnerability is lead by TSWbPrxy.exe which is an ActiveX Control module. The vulnerability allows the attack to bypass Internet Explorer sandbox as it is possible to perform remote attack to gain privileges via a crafted pathname in an executable file.
For Google Chrome, you can read about the freshly CVE-2015-1252 in which the sandbox is violated since it is possible for remote attackers to bypass a sandbox protection mechanism or cause a denial of service (out-of-bounds write) via vectors that trigger a write operation with a large amount of data
It happened a few times during this year's Pwn2Own contest.
Not only that! One team additionally escaped a virtual machine that was running the browser. More details here.
- 289
- 1
- 4
-
link-only answers are only as useful as the lifetime of the link - please include the relevant details from the links in your answer – schroeder Apr 08 '17 at 20:53