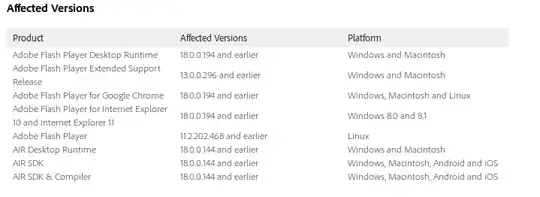
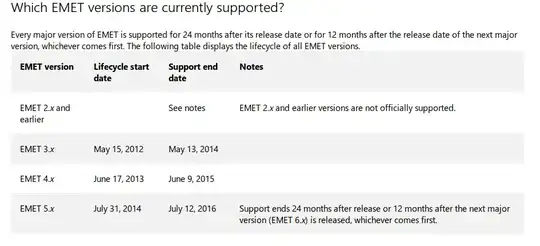
If I were to not update Adobe Flash and instead used the old version (from before the Hacking Team 0-day exploit was published in the internet), in that case, would Microsoft EMET protect me from the latest Hacking Team Adobe Flash 0-day exploit?
- I mean, was the Microsoft EMET effective in protecting user from Hacking Team Adobe Flash 0-day exploit before Adobe patched that vulnerability?
- How effective was Microsoft EMET in prevention of attack with Hacking team Adobe Flash 0-day exploit before Adobe patched that vulnerability?
Malwarebytes' Anti-Exploit was able to prevent that kind of attack. And the big part of Malwarebytes Anti-Exploit is based on Microsoft EMET technology. So it is interesting if Microsoft EMET is able too to prevent that kind of attack as Malwarebytes Anti-Exploit can.
I am NOT asking this question because of some interest in using old version of Adobe Flash. Instead I am asking this questions to get an idea about the effectiveness of Microsoft EMET against 0-day exploits on this particular example of the Hacking Team Adobe Flash 0-day exploit.