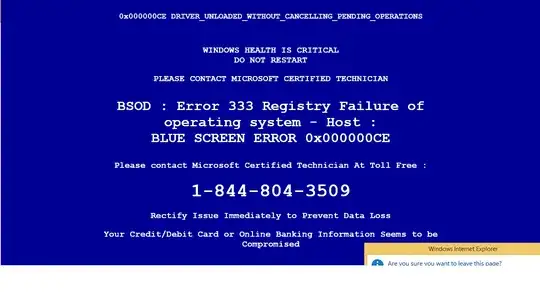
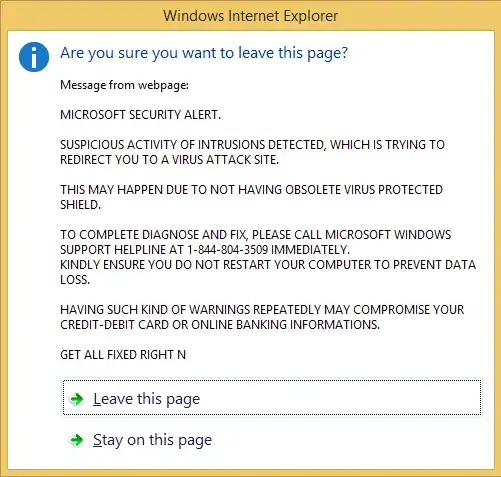
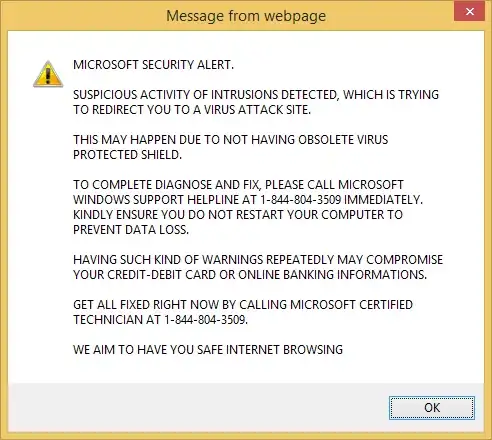
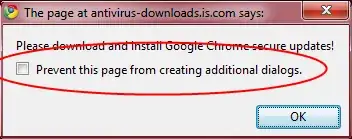
I would suggest using Firefox with NoScript or comparable setup.
NoScript allows you to monitor scripts loaded from websites and selectively allow certain JavaScript to run. That way you can avoid dubious scripts from running. It is especially useful as many malware is not hosted on the website itself , but often through ads or other third party content.
Other than that it is always a good idea to avoid shady websites, have AV product that is up-to-date, always install patches for your browser and OS.
In case you do need to visit websites with questionable reputation, you might want to use a VM with correct configuration to avoid infections of the host. This is not 100% secure but it is pretty good against average threats.
On the contrary of begueradj comment using NoScript prevents drive-by-downloads, when properly configured. Drive-by-downloads use exploits in the browser or it's extensions. Such exploits can be distributed through e.g. JavaScript, Java, Flash, Silverlight among others.
NoScript is able to monitor all content that is referenced and attempted to load by a website you are visiting. Such content can be disallowed and then is not loaded and of course not executed.
It also tries to protect against XSS (Cross-Site-Scripting), CSRF (Cross-Site-Request-Forgery) and clickjacking. Take a look at NoScript's website.
If you whitelisted a site that hosts exploits then of course NoScript cannot protect you (you allowed the execution of scripts manually). This is why you should also follow the other security guidelines.