After port scanning my company's network, I found a lot of open ports. What are the risks that will result out of these ports, if I left them open? And is there any way to handle them without closing them?
-
Could you be slightly more specific about the ports you are talking here? The risk depends highly on this. For example is all `esp` or `IP` open? Is it just `53/udp/IP` or `80/tcp/IP` or `139/tcp/IP` which are opened? – dan Aug 02 '15 at 08:22
4 Answers
What are the risks that will result out of these ports, if I left them open?
As a security good practice, ports should be open only on a need-to-be basis. You are exposing the services that are listening on those ports you left open to exploits. Why? Because a service means something is processing data and thus you are also exposing the vulnerabilities of the applications using those ports.
For example if you let your FTP port open to every one without any restriction rules (firewall) then a hacker could load lot of porn videos to consume lot of space of your server which thing will lead for example to very slow connection to your FTP service. Also lot of ports open expose you more to Trojan Ports.
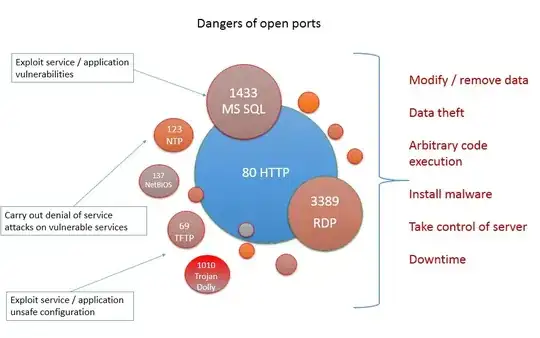
This schema summarizes better the answer to your question:
And is there any way to handle them without closing them?
- Yes, you can leave those ports open but under the condition you have to limit what is allowed to listen on them: that is the job for firewalls. For example, on port 21, allow only the IP address of your home office or home to connect to it and no one else.
- You can leave them open and setting all the closed ones to stealth.
- If you can change a port's number then do it. For example if you can modify the port 21 (FTP) to a higher one (3737 ?), that can lead the hacker to go away because he would start to scan common ports (20, 21 ...) and since port scan takes time, he could be impatient to wait until the scan performs over the 3737 port.
- Use free services that could help you such as this free firewall and from time to time CanYouSeeMe.
- 145
- 1
- 6
-
Regarding canyouseeme: this only provides an "outside view". It is useful when you're interested in what your network looks like from the outside, but based on OP, I'd say he did the scan from the internal network. In that case, regular scans (with OK from the security/IT department, of course!) are a good equivalent. – Rens van der Heijden Aug 02 '15 at 15:06
-
What does the position, size and colour of the circles in the diagram symbolize? Or are they just arbitrary? – user253751 Aug 02 '15 at 22:17
The biggest risk for you is that your company network security detected your portscan. It is a security attack and their countermeasures probably don't consider your wish to remain in your job seriously.
The biggest risk for the company is that a list of numerous open ports means elevated attack surface. Attacking something is a hard thing, but if there are a lot of them, earlier or later an attacker will find his way to get in.
- 2,938
- 6
- 25
- 31
-
Good to remind the 1st risk for the author of the penetration test (legitimate to proceed or not, legitimate to break or not: some servers are so "soft" they can't withstand a `ping` or `nmap`). – dan Aug 02 '15 at 08:16
-
4Did you consider that OP might the the network security guy of his company? :-) – Bergi Aug 02 '15 at 14:25
-
-
@danielAzuelos Thanks. I think, a ping doesn't mean a really usable security risk, but it is highly useful in network testing. In case of nmap, it depends on the circumstances - for example, checking the ports in randomized order, through _tor_, and with a long (also randomized) delay, I don't think that a realistic firewall rule would exist to fiter this out. – peterh Aug 03 '15 at 03:34
-
1@Bergi He didn't says it explicitly, although maybe it is so. His question is imho not on the level of a professional security expert (or he wants to open a bikesched question to collect views and repu). – peterh Aug 03 '15 at 03:35
Open ports are like unlocked doors. The risk depends on what you have in those rooms. If you have some money on a table, then the risk is high. If you have money in a safe, then the risk is medium. And if the safe is bolted to the wall, then the risk is low.
You can close the services behind those ports or you can use a firewall to control or block access to them. It is difficult to manage each host and service, so it is a general practice in companies to put hosts behind a firewall or NAT device. This way, they are not open to access on the internet so risk is reduced because, theoretically, only persons with internal access to the network have access to those hosts and services.
Establishing a security perimeter like this is gradually becoming an ineffective security policy. That is because the security perimeter is becoming porous. New technologies and vulnerabilities allow attackers easy and unexpected access to the internal network. A compromised mobile phone might join the network or an employee might get infected by browsing a malicious website and therefore compromise the perimeter.
As for your question of handling them, there are several ways of reducing the risk, some proactive and some reactive. Segment your network further so certain hosts are not accessible from all the other hosts. A computer in the accounting department should not be accessible without restrictions from any other computer in the company. The reactive method is to log and analyse access inside the company network. This would hopefully deter employees from accessing things that they should not and detect attacks from the outside of the company. This is not bullet proof and would not be effective in a large company.
- 9,797
- 1
- 30
- 50
-
Your metaphor lacks an important aspect: The open door is not necessarily in your home. It may also be the front door of the grocery store you're running to earn your livelihood, or its delivery entrance, or the entrance door to your neighbourhood's public library ... I guess you see what I'm aiming at. – Tilman Schmidt Aug 02 '15 at 21:33
-
I'll change it a bit. I also realised "open" is not a good word. – Cristian Dobre Aug 02 '15 at 21:37
An open port as such is not a security risk. The security risk, if any, is with the service behind the port. The worst case is a port left open unintentionally, because it exposes a service that wasn't meant to be exposed and consequently might not be secured properly.
So the way to deal with the list of open ports you found is:
- Check it against your list of ports that should be open, ie. the services you want to offer.
- Close the ports that should not be open.
- Verify that the services behind the open ports are properly secured as mandated by your security policy.
- 871
- 4
- 7