I have been looking at block ciphers, and I found this:
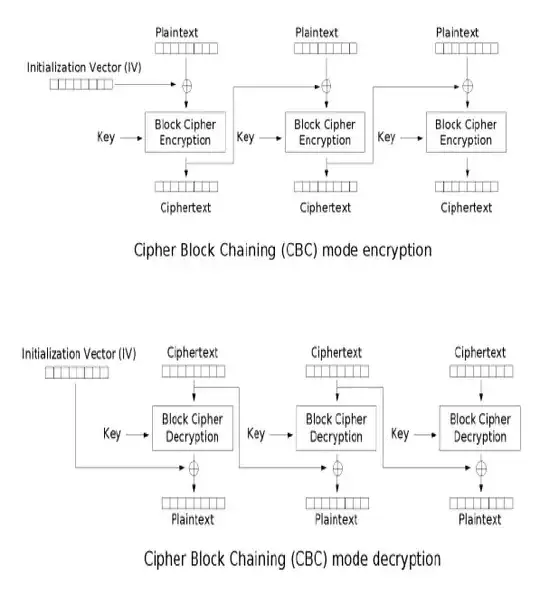
Do the little circles with the plus symbols mean XOR? And how are the plaintext blocks split, and ciphertext blocks combined? Also, how can you XOR text? Can't you only XOR binary? Thank you!
I have been looking at block ciphers, and I found this:

Do the little circles with the plus symbols mean XOR? And how are the plaintext blocks split, and ciphertext blocks combined? Also, how can you XOR text? Can't you only XOR binary? Thank you!
The little circles are indeed XOR.
The size of the blocks depend on the cipher you use, for instance AES-128 has a 128 bit block size (NOTE: the 128 in AES-128 stands for the key size, not for the block size). Note that CBC is Cipher Block Chaining, an operation mode how you use a cipher, not the cipher itself.
The XOR operation is logically on the bits of the plaintext. Everything, also what you are referring to as "text", is internally in any digital computer represented by bits (or bytes=8 bits).
Once the encryption or decryption is done, all bits are put after another. So it would be text from ciphertext 1 then following ciphertext 2 and so on. Depending on byte order the representation might also be the other way around.
The x circles are XOR.
If you are using a DES block size that contains (plain text) is 64 bit, so this divides data into blocks based on encryption algorithm you are using.
Extending the previous answers: