When capturing my SSL session (using Chrome) I have noticed that the server chose TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 (0xc02b) as the cipher-suite and the certificate signedcertificate signature was sha256WithRSAEncryption.
How come the certificate uses RSA while the Cipher-suite is ECDSA?
I found the answer:
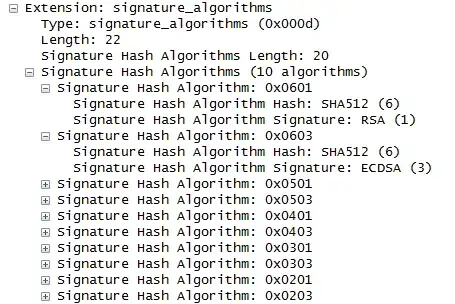
In TLSv1.2, and only in TLSv1.2 - if the client hello include an extension called "signature_algortithm", the server may sign the certificate with any of the methods mentioned in the extension, regardless the cipher-suite it choose to work with.
you can see the extension structure here:
regards, Amigal