I need to convert a pcap-ng/ now a pcap file to a raw file for being able to analyse it with multimon-ng. Any recommendations? It should be possible, but I am not aware how it should be done.
3 Answers
If you want just the ASCII hex dump of all data and nothing else, then you can simply pipe the output of tshark through sed:
tshark -x -r mydata.pcap | sed -n 's/^[0-9a-f]*\s\(\(\s[0-9a-f][0-9a-f]\)\{1,16\}\).*$/\1/p'
- 1,391
- 9
- 16
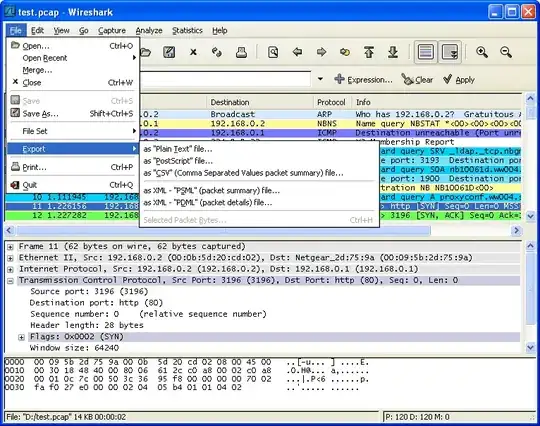
Open Wireshark and go to:
Menu -> File -> Export Packet Dissections -> As Plain Text File
Select the packet range you want to see in your txt file:
If you are interested in the command line solution then you can check tshark documentation.
I don't see any of the transmission modes for Ethernet or for IEEE 802.11 listed in the multimon-ng README file, so I'm not sure how you'd analyze a network capture, done at OSI layer 2, with multimon-ng.
I.e., I'm not sure that you could convert an arbitrary pcap file to something multimon-ng can analyze. If there's some protocol in the pcap file that contains waveforms of radio signals, there might be a way to dump the waveforms into a file that could then be analyzed by multimon-ng, but you can't, for example, turn an 802.11 capture into a radio waveform for the underlying 802.11 PHY - the analog radio signal has long since been turned into a bit stream and further processed by the 802.11 adapter, removing information at that layer.
-
Well, I need to analyse a pcapng- file for hidden information. It has potentially to do with DTMF. I tried it with Wireshark, but couldn't find anything. In the task description it is said, that multimon is a requirement for finding the hidden information. So, I don't really know what else to do. I mean, if you would be willing, I could send you the file. In that case just write to this email: thonikusantonius45@gmail.com – QuintusAurelius Jul 27 '15 at 21:34
-
The only DTMF you'll see in a Wireshark capture comes from various protocols that have "send this DTMF tone" messages in them or protocols that actually send waveforms. In neither of those cases can you do a simple "convert the file to multimon raw format"; you would have to understand the protocols in question and somehow extract the waveforms. I don't have time to do the analysis for you; you'll need to give a *much* more detailed task description in order for anybody to figure out what needs to be done. – Jul 28 '15 at 01:01
-
It isn't a Wireshark capture, but a pre-made file, which intention it is, to have a hidden message between the tones. It is a pcap/pcapng file. I managed to get the hex dump of all the data and I could analyse it using multimon-ng. My problem is that I couldn't analyse the data using the DTMF demodulator. There is a way to get the hidden information, this is for sure, as others managed to do it. There must be a way to get to the hidden message, either by using multimon or some other tool. – QuintusAurelius Jul 28 '15 at 02:10
-
So where are the "tones"? Is this pre-made file just a random set of bits rather than a sequence of packets? Or is does it include a protocol that carries tones? – Jul 28 '15 at 04:56