The Credential Manager stored passwords are managed by the Data Protection API and protected by DPAPI "master keys":
The DPAPI keys used for encrypting the user's RSA keys are stored
under %APPDATA%\Microsoft\Protect{SID} directory, where {SID} is the
Security Identifier of that user. The DPAPI key is stored in the same
file as the master key that protects the users private keys. It
usually is 64 bytes of random data.
This Synactiv presentation has a good overview of DPAPI master keys:
These masterkeys are stored in blobs, each containing:
- a GUID
- a salt
- master key structure (containing master keys)
... and includes this chart, which shows how the protections have changed with each release of Windows:
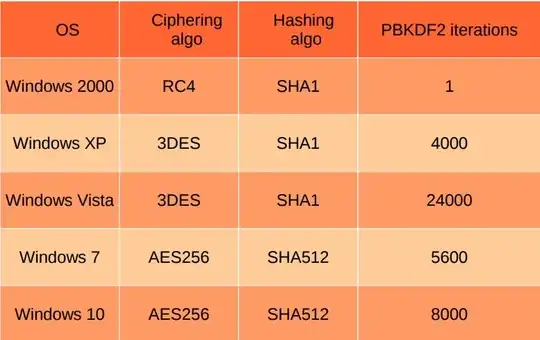
According to that presentation, shared keys can be extracted with mimikatz. Beyond the Windows platform, the dpapick project also supports offline and non-Windows use of the API, and both that project and John the Ripper include DPAPImk2john.py, a script for extracting the masterkey files for cracking purposes. hashcat also supports cracking these DPAPI v1 and v2 masterkey files with that script.
So you should be able to use DPAmk2john.py to extract the master keys, and then crack them to access the credentials.
