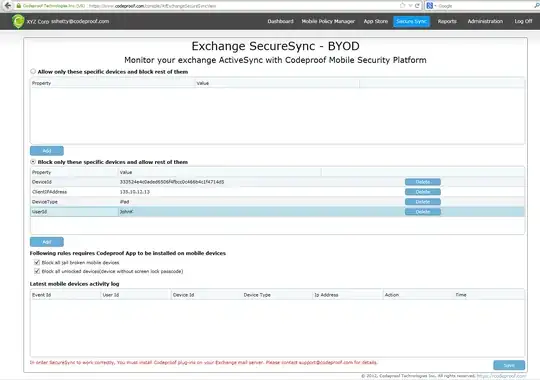
Exchange 2010 / Windows R2
Exchange 2010 includes much of this functionality built-in, and IIS in 2008R2 allows the ability to filter on URLs similar to the 2003 solution below.
- Navigate to OWA via this special URL https://mail.yourcompany.com/ecp/
- Click "Phone and Voice"
- Create a new "device access rule" and configure it to Quarantine or Allow iPhones.
- Note, there is no practical difference between DeviceModel and DeviceFamily.
- (Not personally tested yet) In IISManager, open Request Filtering
- Scroll right to edit the Query Strings.
- Add the appropriate block, according to the URL table below.
Command line junkies can manage devices and default policies as well. As far as I can tell, there is complete feature parity between the ECP and the commandline :
Get-ActiveSyncOrganizationSettings | fl UserMailInsert, AdminMailRecipients, DafaultAccessLevel
Set-ActiveSyncOrganizationSettings -UserMailInsert "Your phone has not been approved, contact IT at x443 to enable email access for this phone" -AdminMailRecipients secnotify@company.com
Exchange 2003 / Windows 2003
We installed Mod_Rewrite (an Apache port to IIS) on each of our Exchange 2003/Front End servers to control access.
Here is the ruleset we are planning on putting into production and will block access to these servers based on the User_Agent field. Note: This ruleset is still in testing and may be revised. If you have comments, please add them.
############## RULE 1 ###############
#
# Exclude Disallowed Devices
#
#Do match and prevent version 4.3.2 (Part 1)
# RewriteCond %{HTTP_USER_AGENT} Apple-iPhone2C1/801.8* [NC,OR]
# RewriteCond %{HTTP_USER_AGENT} Apple-iPhone3C1/808.8* [NC,OR]
# RewriteCond %{HTTP_USER_AGENT} Apple-iPad2C3/808.8* [NC,OR]
#Do match and prevent version 4.3.2 (Part 2)
# RewriteCond %{HTTP_USER_AGENT} Apple-iPhone2C1/801.7* [NC,OR]
# RewriteCond %{HTTP_USER_AGENT} Apple-iPhone3C1/808.7* [NC,OR]
# RewriteCond %{HTTP_USER_AGENT} Apple-iPad2C1/808.7* [NC,OR]
# RewriteCond %{HTTP_USER_AGENT} Apple-iPad1C1/808.7* [NC,OR]
#Do match and prevent version 4.0
RewriteCond %{HTTP_USER_AGENT} Apple-iPhone2C1/801.293.* [NC,OR]
RewriteCond %{HTTP_USER_AGENT} Apple-iPhone3C1/801.293.* [NC,OR]
#Do match and prevent version 3.13 , 3.21 , 3.2
RewriteCond %{HTTP_USER_AGENT} Apple-iPhone2C1/70.* [NC,OR]
RewriteCond %{HTTP_USER_AGENT} Apple-iPhone3C1/70.* [NC,OR]
#Do match and prevent iPad version 3.2 (7b367)
RewriteCond %{HTTP_USER_AGENT} Apple-iPad/702.* [NC,OR]
#Do match and prevent iPad version 3.3X?
RewriteCond %{HTTP_USER_AGENT} Apple-iPad1C1/702.500.* [NC]
RewriteRule ^(.*)$ http://www.nfp.com?rule1 [R=301,L]
############## RULE 2 ###############
#
# Only Permit iPhones and iPads to connect.
# If they got this far, then they are not a banned / blacklisted device.
#
RewriteCond %{HTTP_USER_AGENT} .*iPhone.* [NC]
# Do not alter the URL, and let it come through unmodified.
RewriteRule ^.*$ - [NC,L]
RewriteCond %{HTTP_USER_AGENT} .*iPad.* [NC]
# Do not alter the URL, and let it come through unmodified.
RewriteRule ^.*$ - [NC,L]
############## RULE 3 ###############
#
# Block all other devices, deny rule
#
RewriteRule ^(.*)$ http://www.nfp.com/?rule=3 [L,R=301]
#Device Reference
#iPhone Simulator == i386
#iPhone == iPhone
#3G iPhone == iPhone1C2
#3GS iPhone == iPhone2C1
#4 iPhone == iPhone3C1
#1st Gen iPod == iPod1C1
#2nd Gen iPod == iPod2C1
#3rd Gen iPod == iPod3C1
#Apple-iPad1C1
# The 1st part of that string is always just "Apple-".
# The 2nd part of the string is DeviceType and is defined just
# like the URL above and is either "iPhone" or "iPad".
# The 3rd part of that string is just a delimiter "/".
# The 4th and final part of that string is the software version formatted in a way that Exchange Servers can digest it.
# Here's an example of creating that 4th part of the string using software build version for iPhone which is 7E18 aka iPhone OS 3.1.3.
# The first number from 7E18 (the 7) will become a "7" in the translated string.
# The first letter from 7E18 (the E) will become a "05" since it is the 5th letter of the English alphabet.
# Then you insert a "." (dot).
# The second number from 7E18 (the 18) will become "18". It will be padded with zeros to be 3 digits