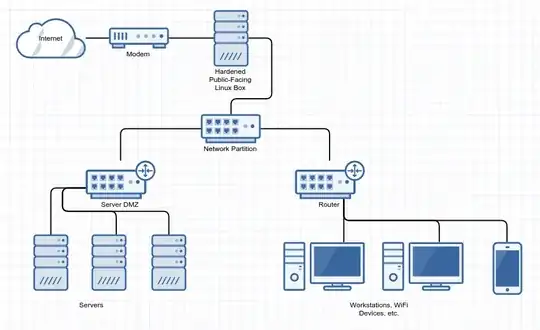
A router is actually a small computer; most of them use the same kind of software as full-fledged servers (typically some Linux variant). As such, it has security holes, that should be patched promptly when discovered. Vulnerabilities that are not fixed might be exploitable and yield remote control to attackers, at which point they can do what they want with the router, and, in particular, see all your internal traffic (unless blocked by further firewalls). The real problem here is that software upgrades on routers is rarely done; it is called a "firmware update" and almost never done.
Most cabled-based ISP provide the modem and tend to consider that the modem is still theirs, not yours. Some will push firmware updates on their own accord, without any warning. Some will try to automatically block at the network level incoming connection attempts that look like attacks on known vulnerabilities. Some don't care.
Some ISP may also claim that by hosting "servers" you are breaching the usage conditions, and then block your Internet access or charge you more. In any case, ISP apply asymmetric bandwidth, with a lot more download than upload. In my experience(*), server hosting at your home, while possible, is not really worth the effort. You have to take care to fly under your ISP radar (or to use one of the rare ISP that do not mind about "server usage"), and the performance is poor. Renting a server somewhere (a simple VPS) is cheap, faster, and way less hassle.
(*) My experience includes running the master DNS for my own domain, and my mail server, from a home machine. I don't do it anymore.