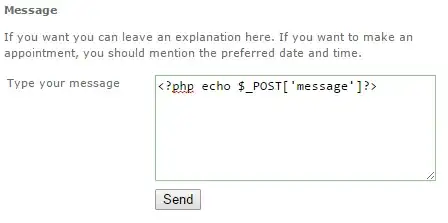
There is no danger in this specific part of the form. It seems that the developers have accidentally escaped the opening and closing PHP brackets, causing PHP code to be displayed as is. Now, this specific form instance doesn't allow us to do anything since it's just text being displayed...
But it teaches us something very important about this site: user input is not properly sanitised.
This means any malicious third-party can create a request that contains arbitrary client-side scripts. This third-party can then convince a user of visiting their own website, and from that website generate a POST request to this vulnerable medical site. Then, the client-side script can be executed by the client you're targeting, within that user's session. If the user is connected to the site and able to perform any privileged operation (such as making a payment, or interacting with the content of the site), you may be able to have them perform this action unwillingly.
Such attacks are called Cross-Site Scripting (XSS) attacks, and are very commonplace unfortunately. See this question on our site and OWASP's own XSS checklist for help with XSS mitigation.