We have a website, https://uk.care.com, that has a GeoTrust multi-SAN cert on it. The cert is up-to-date, using SHA-256, TLS 1.2, etc. When we view the site in Chrome on various desktop systems it shows the green lock in the status bar as expected, and as seen in this screenshot:
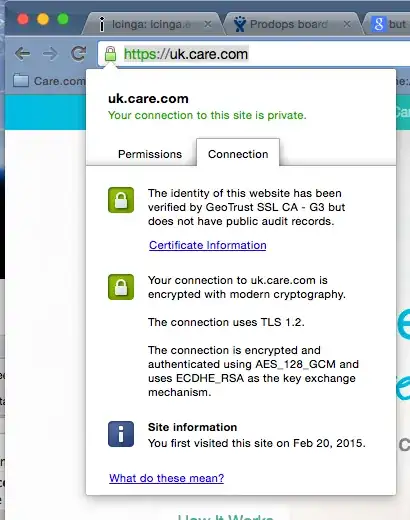
However when we view the mobile version of the site in the latest version of Chrome on an iPhone the lock shows up as yellow in the address bar, but the information regarding the connection is all green, as in this screenshot:
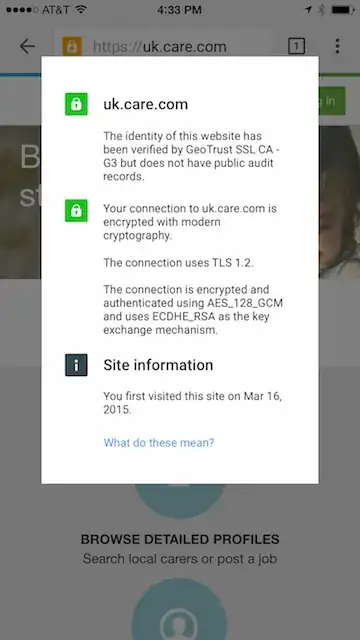
My question is why is Chrome on the iOS device displaying the yellow lock when Chrome on the desktop doesn't? We don't have any issues with this SSL cert in Safari, Opera, or Mercury on iOS nor Firefox or other browsers on desktops.