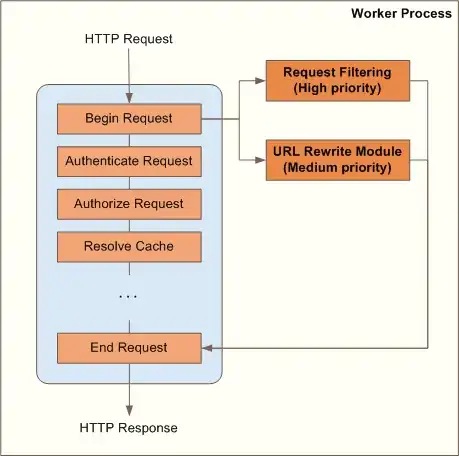
I'm working on implementing an IP-filter which blocks all requests by machines outside our IP-range. This is for an asp.net project (written in c#).
I've read on multiple forums that the safest way to put your IP-filter code is in an HTTP Module which picks up the request early in the aspx-pipeline.
However, I've implemented my IP-filter code directly in the page-load method of the ASPX-pages code behind.
Are there any commonly known security benefits of using a module instead or other reasons why it's considered best practice? I don't know much about ASPX but I'm using IIS 7 if it's any help.