I am starting a new job, and I have the choice to receive a phone from the company, or to bring my own. I am considering using my own phone, to avoid having an extra device, but I want to better understand the consequences of that decision.
I have an iPhone. A more recent one with iOS 8. I will stay with my current wireless carrier.
I understand they can remotely wipe my phone after I leave the company (or if it's lost or stolen), and I'm okay with that, because I already back up every important app.
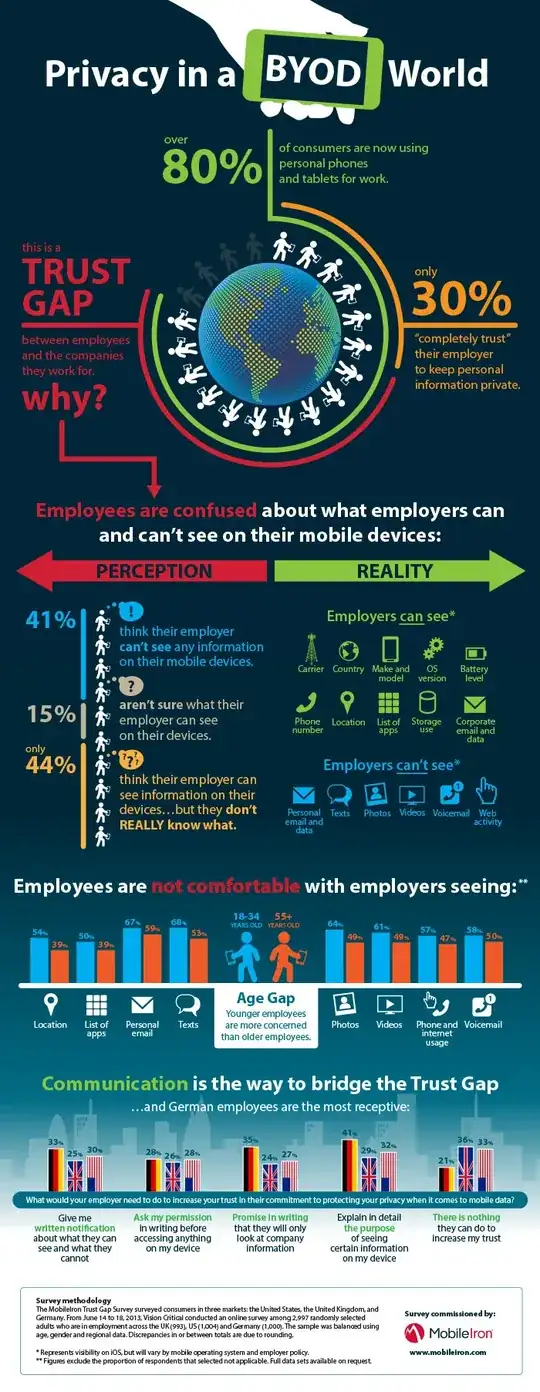
I found this Apple article regarding enterprise iPhones, which states these specific things can and cannot be observed by the company:
Examples of what a third-party management server can and cannot see on a personal iOS device.
MDM can see:
- Device name
- Phone number
- Serial number
- Model name and number
- Capacity and space available
- iOS version number
- Installed apps
MDM cannot see:
- Personal mail, calendars, and contacts
- SMS or iMessages
- Safari browser history
- FaceTime or phone call logs
- Personal reminders and notes
- Frequency of all use
- Device location
(MDM is Mobile device management)
But I'm not certain if this applies to all iPhones in all enterprises.
Concerns/questions
- How exactly is this done? They just configure something in settings, and I supply my lock screen passcode to give them permission?
- Can any of my behavior or data, outside of company-supplied apps, be observed?
- What apps or "root level" utilities can I expect to have installed?
- Will any restrictions be placed on how I can use my phone, or on the apps I can install?
- Is there anything else I need to be aware of?
I found this related question, which discusses BYOD consequences from the company's point of view: What are the problems with bring-your-own-device related to smartphones?