Yes, www.paypal.com is really using RC4 as their preferred cipher, even though this cipher is considered broken for a while. It does support some better ciphers like AES256-SHA but unless the browser explicitly denies support for RC4 (like recent Firefox versions and IE11 do by default) it will use RC4. See also the analysis of SSLLabs.
Interestingly paypal.com (w/o the www) is a different server and supports the more modern GCM ciphers and also enables them by default. It will use RC4 only with older clients not supporting TLS1.2. See also the SSLLabs analysis.
Apart from that none of these servers support any ciphers with forward secrecy, which means if somebody gets hold of the private key of the server (by accident or by law) they can decrypt all the traffic they captured in the last time.
As for www.skype.com: they do support forward secrecy and use it by default, but they don't support any of the modern TLS1.2 AEAD ciphers and thus chrome considers the cryptography obsolete. See Chrome showing cryptography as 'obsolete' and Google Chrome "Your connection to website is encrypted with obsolete cryptography" for more information.
Note that using RC4 as the preferred cipher as done by www.paypal.com is considerable different from offering RC4 as the last resort for clients which don't support better ciphers. RC4 is considered insecure and RFC7465 from 02/2015 goes so far as to explicitly prohibit its use with all versions of TLS:
... However, RC4 has long been known to have a variety of cryptographic weaknesses, e.g., see [PAU], [MAN], and [FLU]. Recent cryptanalysis results [ALF] exploit biases in the RC4 keystream to recover repeatedly encrypted plaintexts. ... As a result, RC4 can no longer be seen as providing at sufficient level of security for TLS sessions.
In the context of www.paypal.com the cipher might probably currently still be safe enough, since not enough data with known plaintext will be transferred with the same key. When used for long-lived TLS based VPN tunnels it might be more problematic. Also, attacks only get better and NSA is known to have top experts in cryptography and might even have better attacks than known to the public.
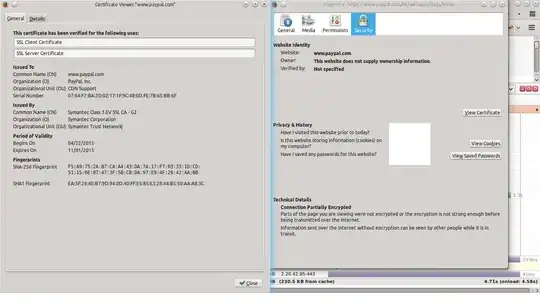
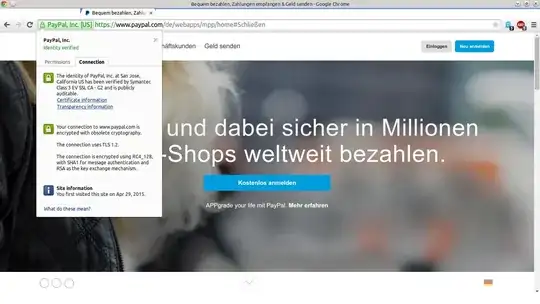 I find it interesting that FF and Chrome give different errors, and that Chrome shows up a green padlock in the address bar, despite the "obsolete cryptography".
I find it interesting that FF and Chrome give different errors, and that Chrome shows up a green padlock in the address bar, despite the "obsolete cryptography".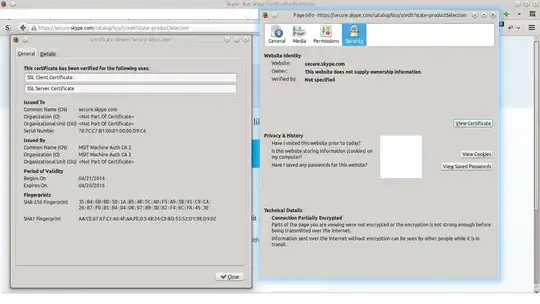
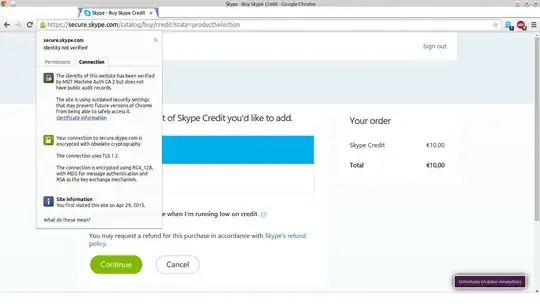 Note that this is not the login page (my browsers accept the https certificate there), it is the page where I want to top up my balance.
Note that this is not the login page (my browsers accept the https certificate there), it is the page where I want to top up my balance.