I've been interested in IT security for a bit (~1 year) and had a bit of experience with NSM as well as web security.
I want to have an overview of the entire industry, with all relevant niches and the association between them. The reasons for this are to (1) identify niches that aren't that known but very approachable (from a curiosity and business perspective) , (2) to understand dependencies between niches, (3) to see where I would actually fit in the best (I'm still not sure of a clear specialization)
When I started to get deeper into the industry "niches" I became overwhelmed seeing that it's a bigger industry than I imagined. I started enumerating every area I could imagine in the field, deriving "niches" from it (e.g. pentesting -> wireless pentesting -> wireless pentesting tools).
I'm having problems differentiating the fields/sub-fields from niches - an example that can be seen in the diagram below would be "secure disposal". Could that be considered a "field" having "secure document shredding" as a "niche" ?
It soon became messy.
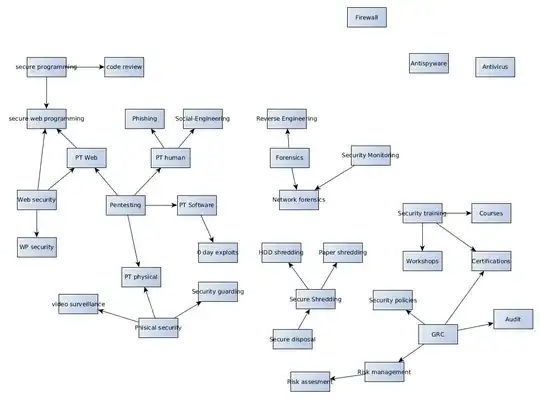
Then I started defining some classification criteria (should have been the first thing), but I'm lacking the words for some of them.
- direction - offensive , defensive
- location - network, host, app
- area - technical, human, process
- management/planning/time perspective - operational, tactic, strategic
At the moment I'm not clear on how to classify the niches. This can end up with multiple diagrams/overviews. Initially I wanted an all-in-one thing, but I'm not clear on how to continue.
Any ideas / words on better classifying / representing this in a visual would be appreciated.