Today I tried a program called Dumpper and the program showed me default WPS of all of my neighbor access points without bruteforcing them, see screenshot below:
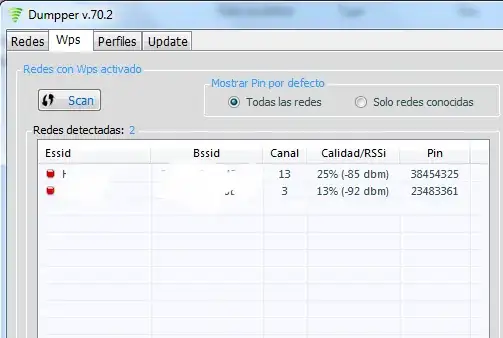
How does this program work?
Today I tried a program called Dumpper and the program showed me default WPS of all of my neighbor access points without bruteforcing them, see screenshot below:

How does this program work?
WPS does not seem to be a well implemented technology. If you reverse engineer the firmware, you may find that the algorithm is MAC based, etc (such as in the case of some D-Link Routers or Belkin).
It also looks like in many cases that implementation weaknesses also permit brute forcing (also see CERT VU#723755) to be done easily.
This is supposedly open source software, so you can examine it to see what is going on exactly, but the code doesn't seem to actually be upon on SF.