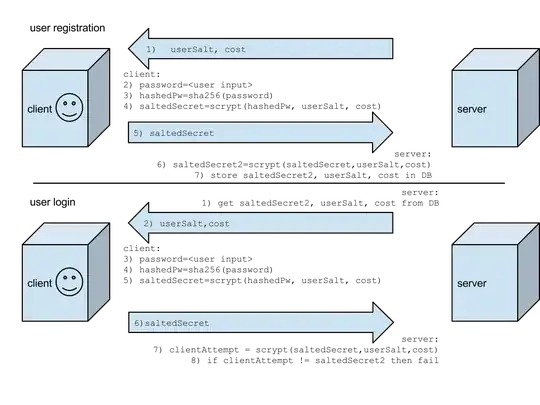
I'm designing a user reg/auth system for a website and came up with this design for password based authentication.
I'd like to know if this is reasonable. (ignoring cookies for caching credentials, oauth, etc)
Some things I built into the design, but not sure how much they "help" security:
in case server db is compromised, hashedPw is sent from client so saltedSecret can be reverified. (hashedPw is not stored on server)
challenge (chalSecret) to prevent replay attack
scrypt cost is adjustable over time, but as I expect to use a javascript implementation of scrypt in browsers maybe it's not such a great feature.
Another question is if I can easily secure the initial sending of the saltedSecret during user registration, but I'm assuming using HTTPS is going to be good enough for that.
If there are ways I can simplify this, please do let me know.
NOTE: please see edit section below for changes that simplify this design.
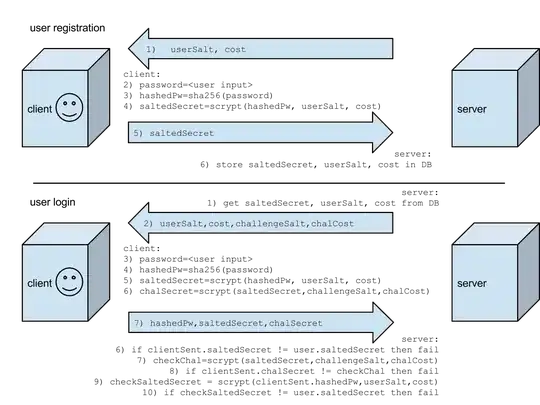
EDIT: Some things that occured to me since posting this:
- TLS protects against replay attacks, so I can remove the entire challenge section.
- on the server side, I should (at minimum) store a hash of the saltedSecret. best is to store an scrypt of it. This has a good side effect of removing the requirement of the user to send the hashedPw during login.
- New diagram with these changes: