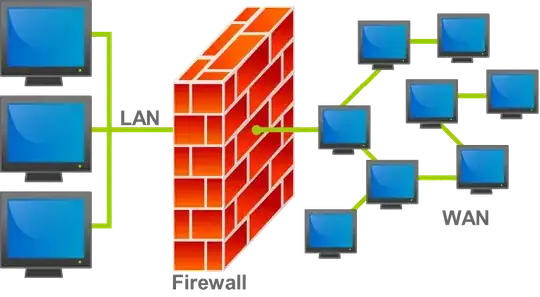
For example. If you're behind a VPN and want to get on on facebook and youtube. Will all outgoing traffic need to make a request to the firewall first?
I don't really know extensively how well a firewall would catch all of this and more specifically how traffic is routed on an internal network.
This is not so I can slack off at work or school, but rather so that I can get a better idea of how exactly these things work below the surface. On a high level I get that the VPN is a "point to point" connection, but if your only source was a school or company network isn't it pretty pointless whether youre behind a vpn or not because 1.) VPN rules/ports may not even be allowed on FW to begin with and
2.) VPN has to send and receive outgoing and incoming requests.
How are these rules different if youre checking your email behind HTTPS?