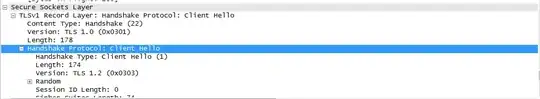
I analysed an live camero's net traffic and found that the client uses both TLS1.0 and TLS1.2 in the handshakings while the server only uses TLS1.0.
How can the handshaking uses both TLSV1.0 and TLSV1.2?Is there a reason for doing so?
1.Is TLS1.0 is sufficiently secure?
2.It uses spdy with TLS1.0, can spdy help to make the transferring more secure?