The WebRTC APIs provide the means to capture audio/video and transfer data to other peers. To get connected to another peer, both peers need to exchange their local session description (SDP) which contains (among other (authentication) data) the IP addresses and (random) port from where the peer can be reached. These IP addresses are found by querying the local network interfaces and via STUN. The WebRTC (RTCPeerConnection) API provides a way to generate this SDP, but not a way to transmit it to the other peer (known as signaling).
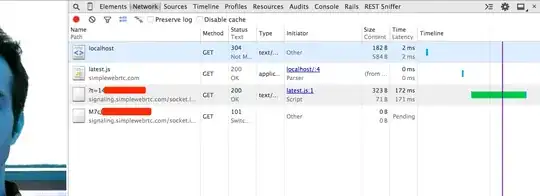
It should be clear that it is extremely unlikely to get connected to a random stranger by accident, because the browser needs to generate the SDP and also has to listen on the local port as stated in the SDP. So, most likely one of your libraries has a built-in signaling mechanism (commonly via WebSockets) to share the SDP with another peer. This turns out to be the case in your specific example: https://bitbucket.org/webrtc/codelab/src/c75c8e837a125441d2ee008c55348ac5a24a85d4/complete/step8/index.html links to http://simplewebrtc.com/latest.js, which defines a default (external) server for signaling (https://signaling.simplewebrtc.com:443/).
If you open the browser's devtools before (re)loading the page, then you can inspect the protocol messages in the Network tab.