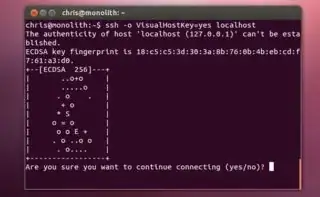
Does the visual fingerprint uniquely identify a server's key?
No; the "visual host key" algorithm does not preserve enough information to give each key a 100%-guaranteed-unique image. But neither does a more traditional fingerprint. ECDSA keys like yours have 256 bits. RSA keys have 2048. But if you count the hex digits in your image, you come up with 32 of them: 128 bits.
Those 128 bits are an MD5 hash of the public key. The MD5 algorithm is hard-coded in a lot of the code that generates fingerprints for display.
The visual host key algorithm (known as "randomart" in the source), takes that MD5 hash and uses it to trace a path. As to how "secure" this is, I'll let the source speak for itself:
If you see the picture is different, the key is different.
If the picture looks the same, you still know nothing.
Isn't this insecure? Isn't MD5 insecure?
If I wanted to trick you with a traditional fingerprint, I wouldn't bother with trying to generate a full MD5 collision of a pre-existing SSH key. That's hard even today.
Instead, I'd generate keys until I found one where the first few digits and the last few digits of the fingerprint matched. Unless you're very disciplined about validating, it wouldn't matter whether the fingerprint was MD5 or SHA256; your eyes would skim the number and it would look "good enough". That's what the visual fingerprint is trying to protect against.
If you're paranoid, then don't use any human-verified fingerprint if you can help it, visual or otherwise. Instead, put a known-good copy of the expected server key in your known_hosts file.
For more information, try:
How is the picture generated?
Again, from the source:
The algorithm used here is a worm crawling over a discrete plane,
leaving a trace (augmenting the field) everywhere it goes.
Movement is taken from dgst_raw 2bit-wise. Bumping into walls
makes the respective movement vector be ignored for this turn.
Graphs are not unambiguous, because circles in graphs can be
walked in either direction.
In more detail, the algorithm works roughly like this:
Start in the middle, and use the hash as a kind of treasure map for where to move next. For each step, take the next two bits in the hash. 00 means move northwest; 01 means northeast; 10 means southwest; 11 means southeast. Hug the wall if you bump into it. Count the number of times you step on each square.
Finally, for each square you stepped on, choose a symbol based on the number of times you stepped on the square, from the following list of 14 symbols: .o+=*BOX@%&#/^. (That's 15 symbols total if you include "S and an E, respectively.