I am not sure what it is called or even if it is possible but here is the scenario I am curious about:
I login to a site that does not use SSL/TLS to do some work (unfortunately I must use this site and have already told the owners to fix it).
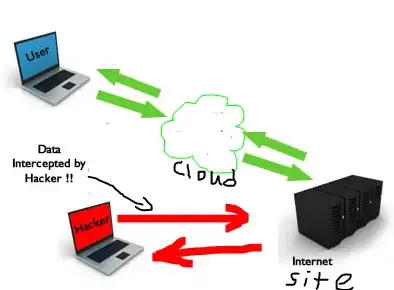
My question is simply can someone (and if so, how) sniff traffic to that site from a network that is not my own.
For instance, I login from my work pc which is presumably in a secure network (IE no one is physically hanging around in the parking lot doing a MitM attack) but can someone not on my work's network simply sniff traffic to the http site itself and simply intercept the POST request there regardless of where I am?
To clarify, I am looking to know if it is just possible without using 'hacks' but instead something like tcpdump. so for instance, I know that if an attacker has compromised the webserver or my work pc they can easily sniff my traffic but at that point, they are no longer outside of my network anyway.
Here is a picture I make.