I seek guidance on interesting issue. Recently I've been searching for password alternatives, not because of the security, but to be more user-friendly.
In one of my projects user receives 128 bits base64 encoded salt as security token, which could be safely transmitted over social networks, messengers, sms, etc. When user decides to perform certain actions, he enters this public salt alongside with secret passphrase.
Now, this 22 random character salt looks unpleasant and raw for the end user, it's difficult to distinguish one security token from another (user can have many), but easy to send, as it is just a string.
My general idea is to:
- Using 128x128 image, each pixel of this image is somehow binded with
corresponding value from
base64with reference to next pixel of a sequence (details currently irrelevant), to produce something that looks like QR code from salt; - Adding, say, gravatar as second layer on top of it, to make it visually recognizable.
My questions:
- Is this approach reasonable from usability point of view? It's harder to send image than string, I suppose.
- Is there any other way to make salt look more user-friendly?
Searched all around for answer. Would greatly appreciate any help.
UPDATE #1
I've found an example on Defuse Security, that generally reflects the scheme that is implemented in my project:
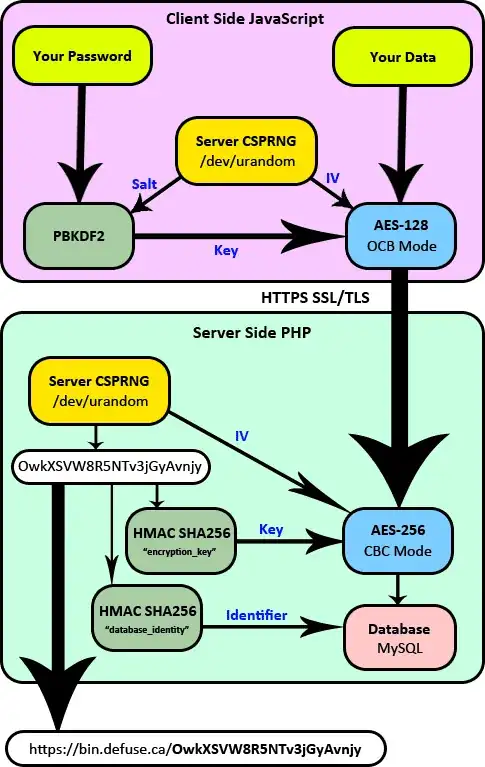
As a result of the encryption process, end-user gets link, and path is actually represents salt - OwkXSVW8R5NTv3jGyAvnjy. This is the ugly stuff I want to transform into image, so it will be secured but still easily distinguishable for users, so my questions remain relevant.
Hope this will help to find out how.
UPDATE #2
I believe that question is misunderstood.
In my project, user have usual password, and some salt, persisted in DB, but that salt is just used as identifier. So, salt is not something that should be kept secret, and generally, salt is not secret. From Andrew Hoffman answer, unless you've got photographic memory, salt is something he has, and password is something he knows.
But the problem is, salt is not user-friendly, it looks heavy, and it's hard to distinguish multiple such salts at a glance. With that I think what salt can be transformed to that will look and feel good. For example, like Google ReCaptcha of version 1 and version 2 - it accomplishes same task, but simple click is more user-friendly than entering some symbols from picture.
I don't want to be annoying with that question, but please, just accept the fact that I'm not inventing my own salt derivation mechanism or security system.